Azure and automation

Create role assignments for different scopes with Bicep
When you create Azure resources with Bicep, you are able to set up role assignments as well. This can be very useful in different scenario’s as it enables you to add an extra layer to your infra as code, which you don’t have to perform manually or through other automation. A role assignment is a resource when you use it in Bicep and can be defined as such, but handling the different scope levels can be a challenge. That is why in this post, I will explain how to create role assignments for different scopes with Bicep.
Before you read on, I recommend you scan through this page in the Microsoft Docs , which gives a great explanation of the different properties of a role assignment. In this post, we will focus on how to handle the scope. To do so, I will walk through all scopes with examples of how a template could be deployed.
Management Group Scope
Let’s start with the biggest scope we have available in Azure resource manager: Management Group. This is how you define the role assignment in Bicep:
To deploy it and set the parameters, you can use different methods. For this post I have used PowerShell. As you can see, you need to define the Id for both the roledefinition and the principalID. To make this a bit easier and more readable, I have made use of Get-AzADUser and Get-AzRoleDefinition
Deployment would go like this:
This deployment would refer to the file rbac-mg.bicep , which it will use to give the user [email protected] the reader role over the management group exampleGroup. Of course you change the values to your own use case.
Subscription scope
So how do we do the same for a subscription? Fortunately, we don’t have to make that many changes. We change the following values:
- Change targetScope = 'managementGroup' to targetScope = 'subscription'
- managementGroup() is changed to subscription()
- managementGroup().id is changed to subscription().subscriptionId
This is all we have to do for the Bicep template. You can find the new template here .
Note: if you don’t define the targetscope, it will by default use the subscription if you use New-AzDeployment. But for readability, you could consider specifying it anyway.
As for the PowerShell deployment, that would now look like this:
The role assignment will be deployed to the current scope of the PowerShell session, which you can find by using Get-AzContext .
Resource Group Scope
The resource scope is very similar to the subscription scope. Again, you change the targetscope and the references from subscription() to resourcegroup() . And for resource groups as well you are able to leave out the targetscope, but you could consider adding it for readability.
To see what the Bicep file would look like, click here .
And deployment would go like this:
Resource scope
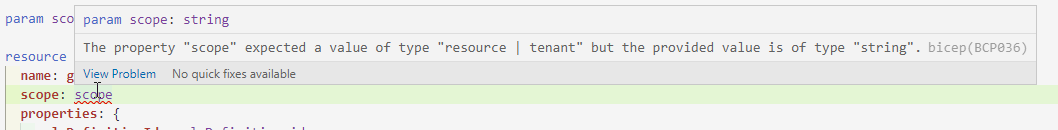
A resource resource role assignment is a little different than the previous deployments. You need to refer to the resource within the role assignment, which you do with the scope parameter. To show how it works, I have used a storage account as an example.
A role assignment to a resource has a different use case than to one of the other scopes. If you are doing an assignment for users, a Resource scope is possible, but can make your environment very complicated. It is recommended to keep the assignments at a higher level. That is different for managed identities or service principles. They need the least amount of principal and could be set on a resource level. An example is a key vault, where you want the role assignment to be very specific.
This is what the bicep file could look like:
I have removed all flexibility in the storage account to keep the focus. In production, you would want some flexibility in the properties of the storage account.
Deployment is the same method as the resource group scope:
Deployment in Modules
This is all cool, but one of the great things about Bicep is the use of modules! So how would you do that? For Management groups, subscriptions, or resource groups, that is pretty straight forward. All of the above files can be used as a module and deployed from a different file with the following syntax:
Now with Resources, it is a little more difficult. As we have seen before, you have to define the scope within the role assignment. You are not able to use a parameter for this scope, as it needs the resource itself as a scope. This makes it more difficult to provide flexibility. Even if you would consider making use of the existing option, you wouldn’t get flexibility as you need to define the resource type there. So how doe we make sure we don’t have to create a separate rbac-module for every resource type?
The answer can be found in the files in the brand new public registry : you make the role assignment a part of the resource module. So in this case, for every storage account you provide the option to add a role assignment in the module file.
But you still need flexibility. Flexibility to not create a role assignment or to create multiple. Again, we can find a great method at the public registry : we use a for loop that is empty by default. If the role assignment is not needed, just don’t add it as a parameter. If you need more than one, you add them as an array. Let’s see how that would look.
The template
Although the registry uses a submodule, I prefer to add it straight to the resource. This is how the module for a storage account would look:
If we want to create the resource without role assignment, we just omit the roleAssignments parameter. If we do want to create one (or multiple), our main.bicep file would refer to it like this:
By using this method for every resource you have in a module, you will have some duplicate code, but you won’t have a separate rbac-module for every resource type. This will keep your module files clean but still provide flexibility.
So this is how you create role assignments for different scopes with Bicep. You can find all the complete Bicep files that are referred to here .
If you want to learn more about Bicep, follow along with the LearnLive series that are running right now: https://aka.ms/learnlive-iac-and-bicep
Related Posts:
I’m also having a problem with the scope of a role assignment. Your post was helpful, but I do have one question. For the example for management group scope, there’s a parameter called “ManagementGroupId”, but it doesn’t seem to be used. I see the role definition is created a the management group level. Is the role assignment also defined at the management group level by default? I assume that’s the case since the targetScope = “managementGroup”. Thanks.
Great article Barbara. Thanks so much!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Easy way to set Azure RBAC roles in Bicep
When deploying resources in Azure using Bicep, occasionally you will have to assign rights to a user or principal to perform certain actions. For example, authorizing an app service to access a storage account.
Initially you would create something like this:
I came up with the following Bicep module which shows a nice way to hide the nasty details such as the role guids in a module.
This makes the Bicep files a lot more readable, especially when you have to assign roles more often.
Creating a module to do this also has the advantage that you can change the scope, for example when the storage account is part of a different resource group.
Cleaned up initial example:
I hope someone has some use for this as well.
Update 18-07-2023: Updated to include principalType in template.
Permissioning Azure Pipelines with Bicep and Azure RBAC Role Assignments

How can we deploy resources to Azure, and then run an integration test through them in the context of an Azure Pipeline? This post will show how to do this by permissioning our Azure Pipeline to access these resources using Azure RBAC role assignments. It will also demonstrate a dotnet test that runs in the context of the pipeline and makes use of those role assignments.

We're following this approach as an alternative to exporting connection strings , as these can be viewed in the Azure Portal; which may be an security issue if you have many people who are able to access the portal and view deployment outputs.
We're going to demonstrate this approach using Event Hubs. It's worth calling out that this is a generally useful approach which can be applied to any Azure resources that support Azure RBAC Role Assignments. So wherever in this post you read "Event Hubs", imagine substituting other Azure resources you're working with.
The post will do the following:
- Add Event Hubs to our Azure subscription
- Permission our service connection / service principal
- Deploy to Azure with Bicep
- Write an integration test
- Write a pipeline to bring it all together
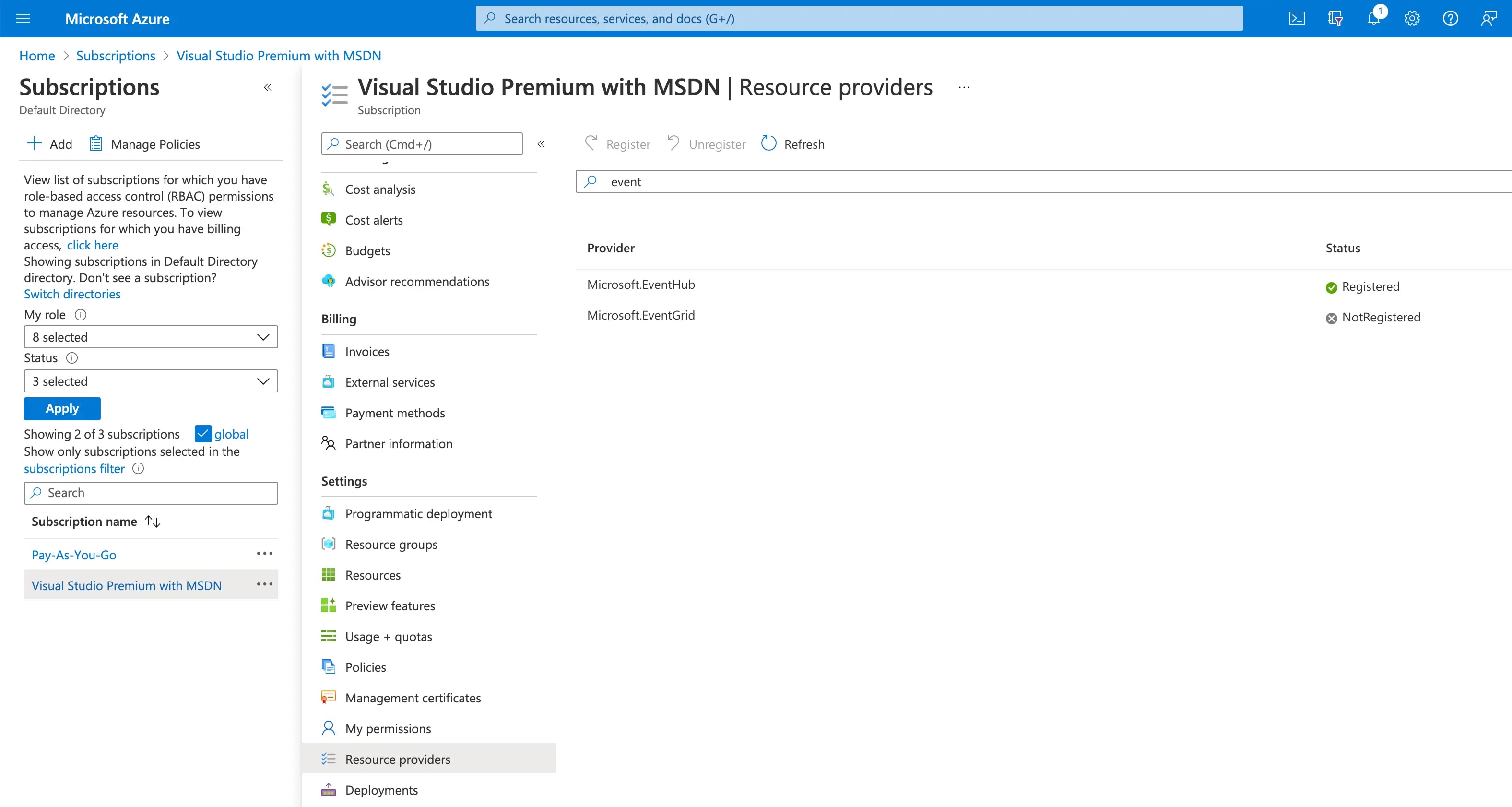
Add Event Hubs to your subscription
First of all, we may need to add Event Hubs to our Azure subscription.
Without this in place, we may encounter errors of the type:
##[error]MissingSubscriptionRegistration: The subscription is not registered to use namespace 'Microsoft.EventHub'. See https://aka.ms/rps-not-found for how to register subscriptions.
We do this by going to "Resource Providers" in the Azure Portal and registering the resources you need. Lots are registered by default, but not all.
Permission our service connection / service principal
In order that we can run pipelines related to Azure, we mostly need to have an Azure Resource Manager service connection set up in Azure DevOps. Once that exists, we also need to give it a role assignment to allow it to create role assignments of its own when pipelines are running.
##[error]The template deployment failed with error: 'Authorization failed for template resource {GUID-THE-FIRST} of type Microsoft.Authorization/roleAssignments . The client {GUID-THE-SECOND} with object id {GUID-THE-SECOND} does not have permission to perform action Microsoft.Authorization/roleAssignments/write at scope /subscriptions/\*\*\*/resourceGroups/johnnyreilly/providers/Microsoft.EventHub/namespaces/evhns-demo/providers/Microsoft.Authorization/roleAssignments/{GUID-THE-FIRST} .'.
Essentially, we want to be able to run pipelines that say "hey Azure, we want to give permissions to our service connection". We are doing this with the self same service connection, so (chicken and egg) we first need to give it permission to give those commands in future. This is a little confusing; but let's role with it. (Pun most definitely intended. 😉)
To grant that permission / add that role assignment, we go to the service connection in Azure Devops:
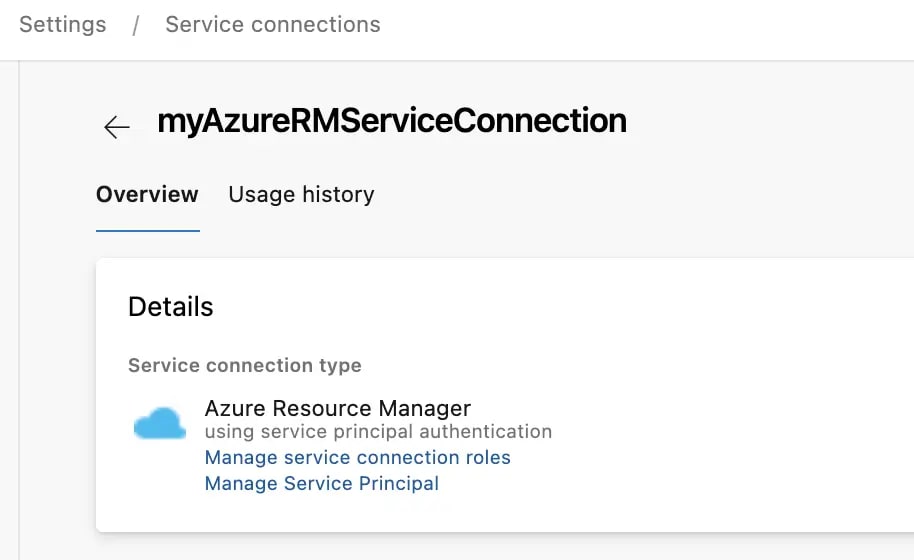
We can see there's two links here; first we'll click on "Manage Service Principal", which will take us to the service principal in the Azure Portal:
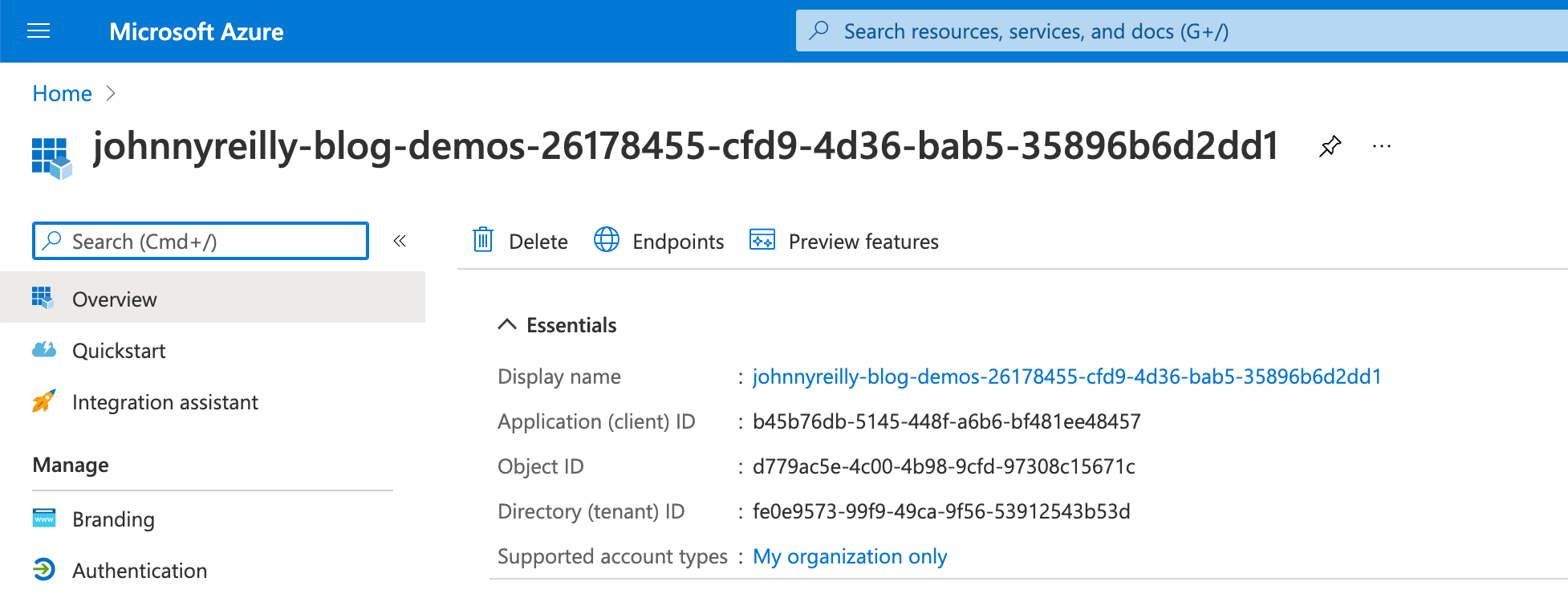
Take note of the display name of the service principal; we'll need that as we click on the "Manage service connection roles" link, which will take us to the resource groups IAM page in the Azure Portal:
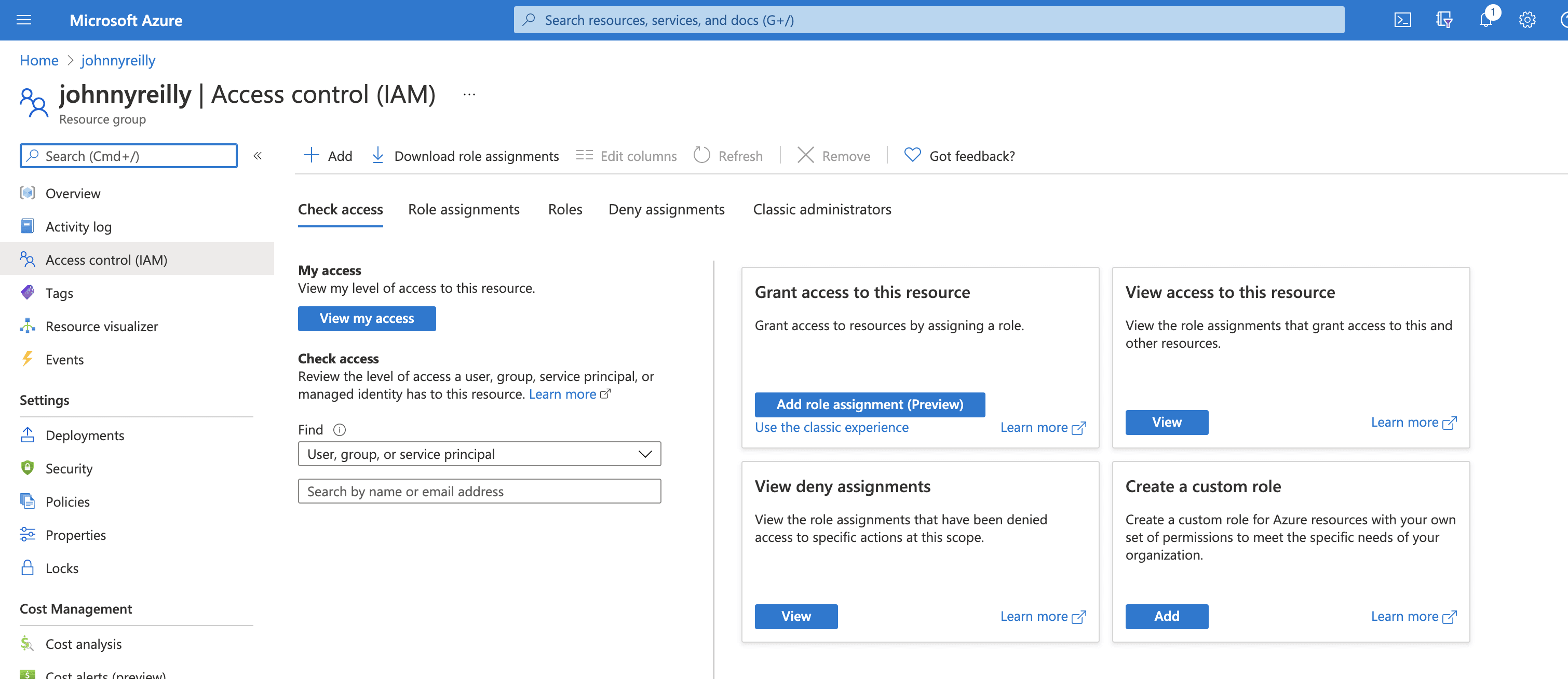
Here we can click on "Add role assignment", select "Owner":
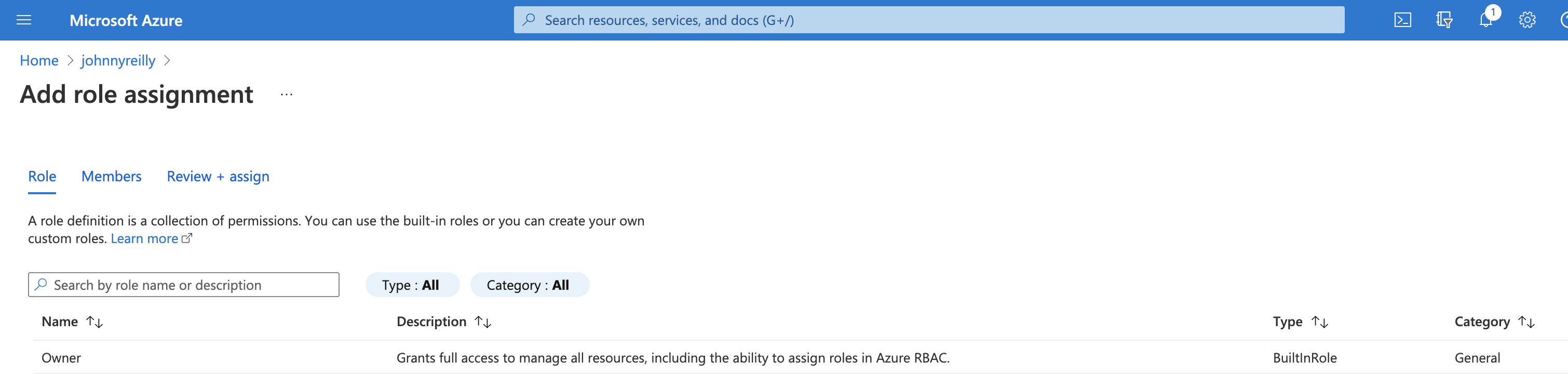
Then when selecting members we should be able to look up the service principal to assign it:
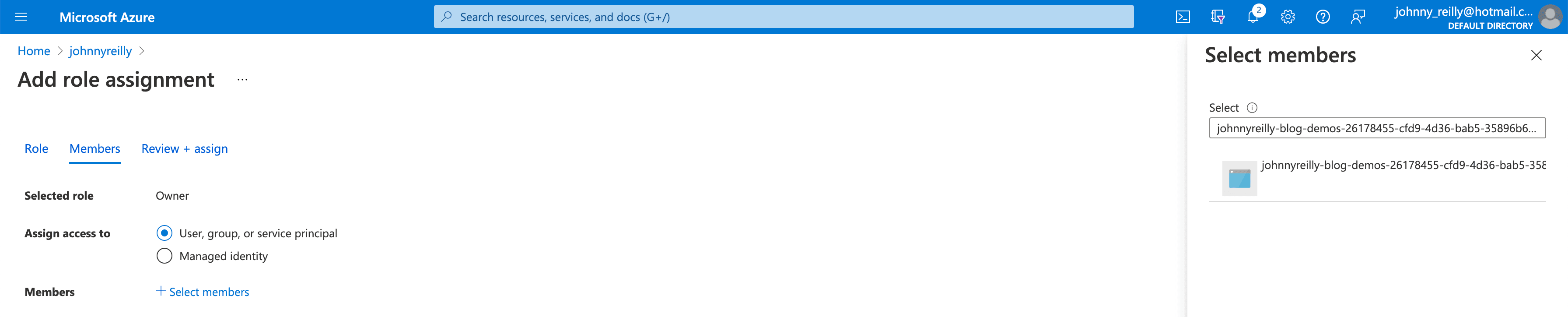
We now have a service connection which we should be able to use for granting permissions / role assignments, which is what we need.
Event Hub and Role Assignment with Bicep
Next we want a Bicep file that will, when run, provision an Event Hub and a role assignment which will allow our Azure Pipeline (via its service connection) to interact with it.
Do note that our bicep template takes the service principal id as a parameter. We're going to supply this later from our Azure Pipeline.
We're now going to write a dotnet integration test which will make use of the infrastructure deployed by our Bicep template. Let's create a new test project:
We'll create a test file called EventHubTest.cs with these contents:
Let's talk through what happens in the test above:
- We read in Event Hub connection configuration for the test from environment variables. (These will be supplied by an Azure Pipeline that we will create shortly.)
- We post a message to the Event Hub.
- We read a message back from the Event Hub.
- We confirm that the message we read back matches the one we posted.
Now that we have our test, we want to be able to execute it. For that we need an Azure Pipeline!
Azure Pipeline
We're going to add an azure-pipelines.yml file which Azure DevOps can use to power a pipeline:
When the pipeline is run, it does the following:
- Gets the service principal id from the service connection.
- Compiles our Bicep into an ARM template
- Deploys the compiled ARM template to Azure
- Installs the dotnet SDK
- Uses the Azure CLI task which allows us to access service principal details in the pipeline to run our dotnet test.
We'll create a pipeline in Azure DevOps pointing to this file, and we'll also create the variables that it depends upon:
- azureResourceGroup - the name of your resource group in Azure where the app will be deployed
- location - where your app is deployed, eg northeurope
- serviceConnection - the name of your AzureRM service connection in Azure DevOps
- subscriptionId - your Azure subscription id from the Azure Portal
- tenantId - the Azure tenant id from the Azure Portal
Running the pipeline
Now we're ready to run our pipeline:
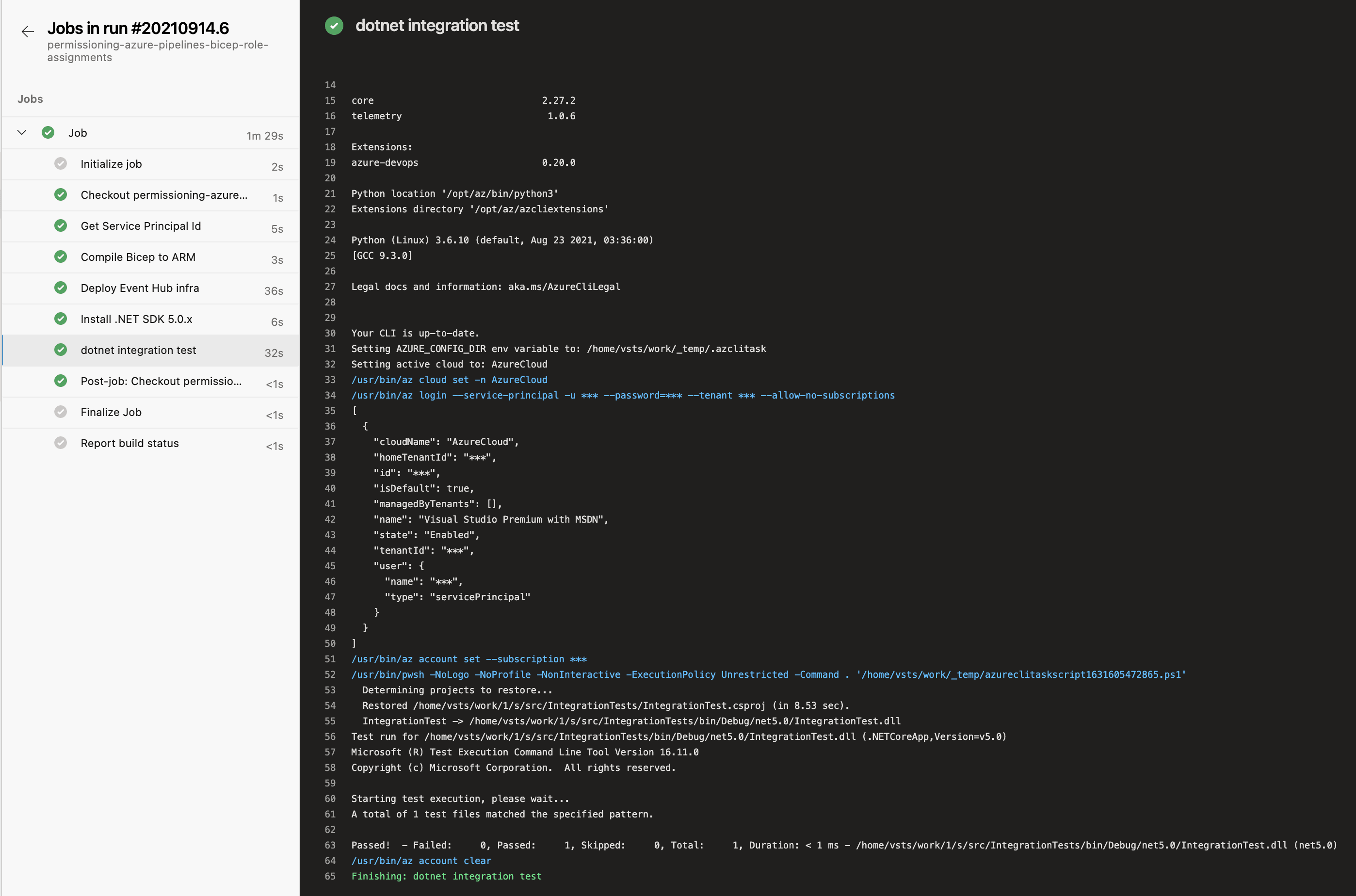
Here we can see that the pipeline runs and the test passes. That means we've successfully provisioned the Event Hub and permissioned our pipeline to be able to access it using Azure RBAC role assignments. We then wrote a test which used the pipeline credentials to interact with the Event Hub. To see the repo that demostrates this, look here .
Just to reiterate: we've demonstrated this approach using Event Hubs. This is a generally useful approach which can be applied to any Azure resources that support Azure RBAC Role Assignments.
Thanks to Jamie McCrindle for helping out with permissioning the service connection / service principal. His post on rotating AZURE_CREDENTIALS in GitHub with Terraform provides useful background for those who would like to do similar permissioning using Terraform.
- Add Event Hubs to your subscription
- Event Hub and Role Assignment with Bicep
- Azure Pipeline
- Running the pipeline

Like often, some automation can make your life just easier! I hope you’ve enjoyed this one!
UPCOMING TRAININGS
CHECK OUT OUR TRAININGS

Azure Integration Services
Azure migration.
- Azure Governance
Azure Security
Azure foundations, recent posts.
- Azure Service Bus vs Event Grid Pull Delivery
- Trying the new Microsoft Applied Skills
- Finally a correct way to configure RBAC for DevOps agents!
- What do the new API Management v2 tiers mean for you?
- Validate payloads in Azure API Management
- Announcement
- API Management
- Architecture
- Azure App Service
- Azure Data Factory
- Azure DevOps
- Azure Event Grid
- Azure Functions
- Azure Kubernetes Service
- Azure Policy
- Azure Resource Graph
- Azure Resource Manager
- Azure Service Bus
- Azure Stream Analytics
- BizTalk Server
- Container Apps
- Geen categorie
- Home Automation
- Microsoft Learn
- Service Bus
MEET THE YOUR AZURE COACH TEAM
Your Azure Coach is specialized in organizing Azure trainings that are infused with real-life experience. All our coaches are active consultants, who are very passionate and who love to share their Azure expertise with you.
Toon Vanhoutte
Azure integration services & serverless.

Wim Matthyssen
Azure infra, security & governance, azure development and ai/ml, azure identity and security, stéphane eyskens, cloud-native azure architecture, geert baeke, azure kubernetes service & containerization, maik van der gaag, azure infrastructure as code & devops, bart verboven, sammy deprez, azure ai, ml & cognitive services, sander van de velde.
Assign Azure Privileged Identity Management Roles using Bicep
Azure Privileged Identity Management (PIM) is a tool that allows you to provide Just In Time (JIT) access to Azure RBAC roles. Using PIM, you can create a role assignment to make a user or group eligible for a role. This assignment doesn’t mean that the user or group has the role, but instead that they can request the role when they need it. When this occurs, the user can trigger an elevation request to be granted the role for a short period (usually hours, but definable). Rules can then be applied to their request, such as requiring approval, requiring a ticket number and so on, and then the rights are granted. PIM is a great tool for removing many permanent access rights to users, but it does require an Azure AD P2 licence for each user.
PIM is an Azure AD feature, so I assumed it wouldn’t be possible to create PIM assignments using Bicep (or ARM), but it is possible. PIM roles are often application or service-specific, so being able to create them as part of your Infrastructure as Code is quite helpful.
Creating PIM Assignments
To create a PIM assignment, we are going to use the Microsoft.Authorization/roleEligibilityScheduleRequests , the full API sec for this can be found here . This object can be used for more than just creating an assignment, it can, in theory, be used to activate an assignment, remove assignments and more. We’ll focus on creating and updating assignments.
To be able to use this, we are going to need a couple of pieces of information:
The object ID of the user or group you want to assign the role to. This can be found by looking at the user or group in AAD. You’re looking for the object ID field
The complete ID of the role you want to assign. This is usually in the format:
Subscription ID is the ID of the subscription holding the role you want to assign. The role ID is the GUID of the role. You can find the GUID’s for all the built-in roles in the MS docs here , or you can also use the handy AzRoleAdvertizer site . If you’re applying the assignment at the management group rather than subscription or resource, you will replace this with the ID of the management group role.
With this information, we can create the Bicep code we need. First, we need to get the start date for the role in the correct format. The format is 2022-04-10T14:40:08.067566 but fortunately, the Bicep utcNow function gets this in the correct format, so we can use that. This function can only be used as a default value for a parameter, so we need to create a parameter in our template that we assign this to and won’t override in the future.
Now we have that we can create the actual resource:
A few things to note:
- The name needs to be a GUID, so I am using the guid function to generate one, passing the resource group and a string as a seed to ensure a consistent GUID generation should I run this again
- The request type is set to AdminUpdate. This will create a role if it doesn’t exist and update it if it does. You can use AdminCreate if you want only to create it.
- The schedule info section is setting that the user or group should be eligible to elevate for a year (the max allowed) before the role needs to be reviewed
- I have set the scope to be the resource group. This defines that the PIM role should be for this resource group only. If I wanted to assign rights to elevate over a whole subscription or management group, then I would adjust the scope
The whole template looks like this:
Once deployed, you should be able to go to the PIM UI in the portal and see that the designated user or group is now eligible to elevate to this role.
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
RBAC - Modification / Removal in BICEP #4432
{{editor}}'s edit
Harirajan2014 sep 14, 2021.
Beta Was this translation helpful? Give feedback.
Can you clarify a bit more about the scenario of needing to add a role assignment, then quickly remove it? Is this specific to assigning blueprints?
Once we have stacks, in two separate deployments of a stack you could do this:
Stack at Time 0:
- Role assignment:
Updated stack at Time 1:
That will remove the role assignment since it is no longer in the bicep/template code.
That's more of a scenario of needing the role assignment at one point, but then deciding it's not needed later, so you update the definition of the goal state. What's a bit more unusual about this scenario is that you know at the beginning you won't need the role assignment eventually.
cc @bmoore-msft …
Replies: 2 comments · 7 replies
Brwilkinson sep 14, 2021 maintainer, alex-frankel sep 14, 2021 maintainer.
brwilkinson Sep 16, 2021 Maintainer
HariRajan2014 Sep 17, 2021 Author
alex-frankel Sep 22, 2021 Maintainer
bmoore-msft Sep 22, 2021
Harirajan2014 sep 23, 2021 author.
- Numbered list
- Unordered list
- Attach files
Select a reply
- Election 2024
- Entertainment
- Newsletters
- Photography
- Personal Finance
- AP Investigations
- AP Buyline Personal Finance
- AP Buyline Shopping
- Press Releases
- Israel-Hamas War
- Russia-Ukraine War
- Global elections
- Asia Pacific
- Latin America
- Middle East
- Election Results
- Delegate Tracker
- AP & Elections
- Auto Racing
- 2024 Paris Olympic Games
- Movie reviews
- Book reviews
- Personal finance
- Financial Markets
- Business Highlights
- Financial wellness
- Artificial Intelligence
- Social Media
Pirates designate LHP Josh Fleming for assignment one night after a poor relief performance
Pittsburgh Pirates pitcher Josh Fleming throws during the seventh inning of a baseball game against the Milwaukee Brewers Monday, May 13, 2024, in Milwaukee. (AP Photo/Morry Gash)
Pittsburgh Pirates starting pitcher Josh Fleming delivers during the first inning of a baseball game against the Milwaukee Brewers in Pittsburgh, Wednesday, April 24, 2024. (AP Photo/Gene J. Puskar)
- Copy Link copied
MILWAUKEE (AP) — Left-handed pitcher Josh Fleming was designated for assignment by the Pittsburgh Pirates on Tuesday, one day after he allowed six runs while getting just three outs in a relief appearance.
The Pirates recalled right-hander Ryder Ryan from Triple-A Indianapolis to fill Fleming’s spot.
“We needed a bullpen arm,” Pirates manager Derek Shelton said Tuesday before a game with the Milwaukee Brewers. “We have other guys that are available tonight and we need the innings. Josh became the odd man out.”
Fleming, who turns 28 on Saturday, had a 1-1 record and a 5.68 ERA with one save in 17 appearances with the Pirates this season. He had pitched for the Tampa Bay Rays from 2020-23.
After heading into April 30 with a 1.29 ERA, Fleming had given up 11 runs – 10 earned – over five innings in his last five appearances.
In the Pirates’ 8-6 victory over the Brewers on Monday night, Fleming allowed a grand slam to Jake Bauers and gave up a two-run double to Willy Adames.
He started the seventh inning with the Pirates ahead 5-0 before allowing Adames’ double. After the Pirates extended their lead to 7-2 in the top of the eighth, Fleming faced four batters in the bottom of the inning without retiring any. Blake Perkins and Gary Sánchez opened with singles, and after Joey Ortiz reached on an error by shortstop Oneil Cruz to load the bases, Bauers hit a shot over the right field wall to cut Pittsburgh’s lead to 7-6.
Five of the six runs Fleming allowed were earned.
Ryan, 29, has gone 1-0 with a 3.00 ERA in nine relief appearances with Pittsburgh this season. He also has an 0-0 record and 3.86 ERA in five games with Indianapolis.
“This guy throws a sinker that really does a nice job of getting ground balls when he executes it,” Shelton said.
AP MLB: https://apnews.com/hub/mlb

Cardinals capture series win over Angels, but roster construction concerns remain

ANAHEIM, Calif. — The St. Louis Cardinals did what they needed to do during their three-day visit to Angel Stadium.
They took two of three from the feeble Los Angeles Angels , who entered the series with a 15-26 record, one game worse than the Cardinals. An eight-run seventh inning propelled them to victory in a bullpen game on Monday, and after coughing up a five-run lead on Tuesday, they rallied in the later innings for a comeback win. After a dismal series against the Milwaukee Brewers , St. Louis somewhat righted their ship, keeping them afloat for another week.
But are they built to last?
Goldy gets us on the board in the 6th! #ForTheLou pic.twitter.com/wVkR2oFq3E — St. Louis Cardinals (@Cardinals) May 16, 2024
Let’s take a look at Monday’s game, for example. Despite Matthew Liberatore finding success as a multi-inning left-handed arm in relief, the Cardinals opted to start him in a bullpen game for the second time this year. He allowed four earned runs over 3 1/3 innings but was let off the hook after a valiant comeback by the offense.
Advertisement
The problem is not that Liberatore was chosen as a spot starter. He was drafted as a starting pitcher and is versatile enough to slot in on short notice. The problem is that he shouldn’t have to.
When the Cardinals pieced out their offseason last winter, they rightfully emphasized pitching. To John Mozeliak’s credit, the offseason additions he brought in, both as starters and relievers, have been largely successful. Sonny Gray has dazzled atop the rotation and Kyle Gibson has made for a strong supporting act behind him. Rarely have the Cardinals not been in ball games when Gray, Gibson or Lance Lynn take the mound. Andrew Kittredge and Ryan Fernandez are valuable assets in the bullpen. Keynan Middleton , who began a rehab assignment with Double-A Springfield on Tuesday, isn’t far behind.
One could argue Mozeliak’s pitching blueprint could hardly have played out better. Because the starting pitching has been able to regularly log at least six innings an outing, and because the bullpen is so vastly improved, St. Louis has been able to essentially lock down wins with their relievers.
With a lead, manager Oli Marmol can opt for the right-handed Kittredge or left-handed JoJo Romero based on the opposing lineup. He can do the same when trailing, using Fernandez or Liberatore. And once the game gets to Ryan Helsley , who with his 1.35 ERA and 13 saves has been one of the league’s best closers, it’s basically a wrap. The bullpen has been so dependable that the Cardinals were able to rest a struggling Giovanny Gallegos (who is now on the injured list with a shoulder impingement), someone they were counting on for high-leverage spots.
But by plugging Liberatore into the rotation as a spot starter, the Cardinals are subtracting value from their strongest area. For the second time this season, St. Louis opted to start Liberatore in a bullpen game with a pitch limit of 50 because they had no other viable option. Essentially, they took an important piece from their most successful portion of the roster and made the rotation and the bullpen weaker in the process. And yet, after being without Steven Matz for two full weeks, the Cardinals have yet to find a consistent answer as to who will take his place in the rotation. The Cardinals will honor the off day on Thursday and will start Kyle Gibson on Friday against the Boston Red Sox with Miles Mikolas slated for Saturday. They do not have a starter listed for Sunday.
Some explanation as to how the Cardinals got here should be provided. Liberatore entered spring training alongside Zack Thompson competing for the sixth-starter role. When Gray missed the first two starts of the season with a hamstring strain, St. Louis decided both Liberatore and Thompson would make the Opening Day roster, Thompson as the No. 5 starter and Liberatore in the bullpen. But Thompson struggled to maintain velocity — his fastball dropped nearly 5 mph, topping out at 91 mph. When Gray returned, Thompson was optioned to Triple-A Memphis. The Cardinals attributed the drop in velocity to a drop in Thompson’s weight. He’s now in the midst of a lengthy recovery program as he works to build his strength and arsenal back up, and is no longer an option to spot start.
The Cardinals hoped they would not need a sixth starter for the next few weeks, while Thompson and Andre Pallante iron out their kinks and build up from an innings perspective. When Matz felt his lower back tighten up in between starts in late April, he decided to push through it. This is common practice — players play through general tightness and soreness on a near-daily basis.
Except when Matz took that next start it was clear he wasn’t right. He lasted fewer than four innings and landed on the 15-day IL with a protruding disk in his lower back. Matz was initially given an injection, with a return to baseball after a couple of weeks the best-case scenario. Instead, after his bullpen session last week, Matz ended up needing a second injection, meaning he’ll miss at least a month from his first missed start, if not more.
Now St. Louis is scrambling to find a fill-in and has no sound answer. That Liberatore was their best option isn’t a shot at him or his performance. It’s an indictment on both the 40-man roster and the pitching development in Triple A. Thompson and Pallante aren’t stretched out to start (neither are they mechanically sound enough currently to do so) and the Cardinals don’t want to rush up prospects like Sem Robberse , Adam Kloffenstein or Gordon Graceffo (and they aren’t knocking on the door based on their numbers anyway).
“(Liberatore) gives us our best chance,” Marmol said repeatedly before Monday’s game. “He’s the better pitcher.”
Concerns on the bench
The holes in the roster aren’t limited to the pitching side, either. Let’s take a look at the Cardinals bench.
St. Louis is without two of its most valuable assets. Tommy Edman is progressing (albeit slowly) after complications from offseason wrist surgery. He’s working through his swing program and has hit all of his benchmarks but remains far from a rehab assignment. Willson Contreras’ freak accident has sidelined him likely until the All-Star break.
But most of the currently rostered names were not part of the organization’s major-league plans this year. Michael Siani was supposed to serve as a defensive replacement, now he’s the starting center fielder. Alec Burleson , Dylan Carlson , Iván Herrera and Matt Carpenter were supposed to serve as role players; instead, they’re seeing daily action.
The 40-man names in Triple A ( Luken Baker , José Fermín , Alfonso Rivas ) are not top prospects, nor are they anything more than organizational depth pieces from a roster standpoint. Prospects Thomas Saggese and Victor Scott II certainly have potential but neither is ready for the major leagues — and the Cardinals saw this already when Scott was rushed to the majors three days before Opening Day out of need. Jordan Walker , optioned to the minors in mid-April, will remain there as he works to regain both feel and confidence with his swing.
With the way Marmol’s lineup is constructed, there have been several instances in which his only right-handed bench bat is his backup catcher, Pedro Pagés . Marmol has been forced to burn his designated hitter several times this season to play a matchup with opposing hitters, in part because the Cardinals are carrying seven left-handed hitters. Many of them are one-dimensional ( Brandon Crawford , for example, plays once a week as the backup shortstop) or are underperforming (the at-bats have looked better lately, but Nolan Gorman , Lars Nootbaar and Brendan Donovan all have an OPS under .700).
The absence of productive right-handed bats showed up in Tuesday’s game, when Marmol started four lefties against left-hander Reid Detmers , even with switch-hitting Carlson getting the start in right field and Carpenter getting the night off. Left-handed Burleson, who was on the cusp of making the roster out of spring, batted fifth. Again, this is not a slight at Burleson — whose go-ahead two-run home run in the seventh inning made the difference in St. Louis’ 7-6 win, and whose overall play has been strong of late. But you’ll be hard-pressed to find a fourth outfielder batting fifth against the same-handed pitcher on any playoff-caliber major-league roster.
They weren’t expected to be World Series contenders, but the Cardinals certainly expected to be better than this. Their starting core has struggled as a unit, and yes, it is ultimately the manager and his staff’s responsibility to ensure they get the most out of their players. But the team’s true problems run much deeper than that.
The Cardinals take the field every day hoping Band-Aids will stop the bleeding. That strategy was successful over a three-game stint in Anaheim. But is it sustainable for the entirety of a season?
That’s the real question for the Cardinals this year.
(Photo of Iván Herrera and Matthew Liberatore: Ronald Martinez / Getty Images)
Get all-access to exclusive stories.
Subscribe to The Athletic for in-depth coverage of your favorite players, teams, leagues and clubs. Try a week on us.

Katie Woo is a staff writer for The Athletic covering the St. Louis Cardinals. Prior to joining The Athletic, Katie spent two years covering the minor leagues as an editorial producer for MiLB.com and spent the 2018 MLB season covering the San Diego Padres as an associate reporter for MLB.com. She is a graduate of Arizona State University and originates from Northern California. Follow Katie on Twitter @ katiejwoo

IMAGES
VIDEO
COMMENTS
Azure role-based access control (Azure RBAC) is the way that you manage access to Azure resources. In this quickstart, you create a resource group and grant a user access to create and manage virtual machines in the resource group. This quickstart uses Bicep to grant the access. Bicep is a domain-specific language (DSL) that uses declarative ...
name: resourceName. } Now, if I want to make this role assignment specific to one resource type, it's easy enough to solve: targetScope = 'resourceGroup'. @description('The ID of the principal receiving the role assignment') param principalId string. @description('The ID of the role definition to assign to the principal') param roleDefinitionId ...
A resource resource role assignment is a little different than the previous deployments. You need to refer to the resource within the role assignment, which you do with the scope parameter. To show how it works, I have used a storage account as an example. A role assignment to a resource has a different use case than to one of the other scopes.
If so, I unfortunately do not know of a way to do that in Bicep. I know you can download a CSV or JSON file of all the role assignments on a resource in the Azure Portal, which might be of some help. Alternatively, you can use the AzCLI to get what you want using: az role assignment list --scope <resource id> --role "<role name>" Hope this helps!
This post will show how to do this by permissioning our Azure Pipeline to access these resources using Azure RBAC role assignments. It will also demonstrate a dotnet test that runs in the context of the pipeline and makes use of those role assignments. We're following this approach as an alternative to exporting connection strings, as these can ...
A pure Bicep approach, user-friendly, but quite some work to setup; Generate the Bicep module. I wanted to have a Bicep module to perform role assignments on resource group level, similar like Jos described in his blog post. It had to support all available Azure roles.
This is a simple demo of how to (ab)use scoping and extension type resources in Bicep with a main.bicep that deploys at the subscription scope the option to create a role assignment at either subscription, resource group or resource scope with one template.. Depending on the type parameter the main template invokes one of three templates as modules. . Note that due to missing support (see ...
Azure Privileged Identity Management (PIM) is a tool that allows you to provide Just In Time (JIT) access to Azure RBAC roles. Using PIM, you can create a role assignment to make a user or group eligible for a role. This assignment doesn't mean that the user or group has the role, but instead that they can request the role when they need it.
August 19, 2021. This will be a quick one! A colleague asked me if it was easier to use user assigned managed identities in Bicep versus ARM. Well, challenge accepted! After about 45 minutes of hacking, I created the following: @description('Web app name.') @minLength(2)
Assigning RBAC via Role Assignment Module. #5678. Trying to have a module to handle RBAC assignment. Thought this was a good use case where multiple assignments can be handled via a single module. This would include having to pass the scope of the assignment. Per ARM documentation this could be done as a string.
You need to use this in a module that targets the resourceGroup you want to assign permissions to. So you need to have 3 files - one is where you create the resource groups, second is where you put the roleAssignments resource. Then, from the first one call the module (s): module rgLaDevPermissions 'devPermissions.bicep' = {.
Role Def; Role assignment: Updated stack at Time 1: Role Def; That will remove the role assignment since it is no longer in the bicep/template code. That's more of a scenario of needing the role assignment at one point, but then deciding it's not needed later, so you update the definition of the goal state.
Hunt for suspicious Azure Resource Management (ARM) activities. One of the most common resources deployed by attackers in compromised subscriptions are virtual machines. Let's hunt for a new external user who has deployed at least X virtual machines: ... Suspicious role assignment in Azure subscription; Access elevation by risky user; Risky ...
A now-extinct stretch of the Nile River once flowed close to Egypt's Great Pyramid and likely played a key role in the construction of ancient monuments before disappearing, according to new ...
The Pittsburgh Pirates have designated left-handed pitcher Josh Fleming for assignment by the Pittsburgh Pirates one day after he allowed six runs while getting just three outs in a relief appearance. ... "We needed a bullpen arm," Pirates manager Derek Shelton said Tuesday before a game with the Milwaukee Brewers. ... AP's Role in ...
I try to create two role definitions and two role assignments to one Azure CosmosDB SQL API account using Bicep template. I decompiled below arm template with az bicep decompile: https://github.com...
Some explanation as to how the Cardinals got here should be provided. Liberatore entered spring training alongside Zack Thompson competing for the sixth-starter role. When Gray missed the first ...
The Azure functions deployment is running under a managed identity. And as we want to deploy everything automatically, using Azure Bicep, I want to automatically give the correct role assignment on the Service Bus namespace (or entities) for that managed identity, in an Azure Bicep file. But I don't seem to find out how to do that.
Azure Bicep - Role Assignment in a different subcription. 2 Secret scoped role definition and assignment using bicep. Load 7 more related questions Show fewer related questions Sorted by: Reset to default Know someone who can answer? Share a link to this ...