Accessibility Links
- Skip to content
- Skip to search IOPscience
- Skip to Journals list
- Accessibility help
- Accessibility Help
Click here to close this panel.
Purpose-led Publishing is a coalition of three not-for-profit publishers in the field of physical sciences: AIP Publishing, the American Physical Society and IOP Publishing.
Together, as publishers that will always put purpose above profit, we have defined a set of industry standards that underpin high-quality, ethical scholarly communications.
We are proudly declaring that science is our only shareholder.

Research on Big data Security privacy Protection based on cloud Computing
Tongtong Xu 1 and Lei Shi 2
Published under licence by IOP Publishing Ltd Journal of Physics: Conference Series , Volume 2083 , 2. Computational Science Citation Tongtong Xu and Lei Shi 2021 J. Phys.: Conf. Ser. 2083 042077 DOI 10.1088/1742-6596/2083/4/042077
Article metrics
139 Total downloads
Share this article
Author e-mails.
Author affiliations
1 School of Management, Tianjin University of Technology, Tianjin, China
2 School of Management, Tianjin University, Tianjin, China
Buy this article in print
Cloud computing is a new way of computing and storage. Users do not need to master professional skills, but can enjoy convenient network services as long as they pay according to their own needs. When we use cloud services, we need to upload data to cloud servers. As the cloud is an open environment, it is easy for attackers to use cloud computing to conduct excessive computational analysis on big data, which is bound to infringe on others' privacy. In this process, we inevitably face the challenge of data security. How to ensure data privacy security in the cloud environment has become an urgent problem to be solved. This paper studies the big data security privacy protection based on cloud computing platform. This paper starts from two aspects: implicit security mechanism and display security mechanism (encryption mechanism), so as to protect the security privacy of cloud big data platform in data storage and data computing processing.
Export citation and abstract BibTeX RIS
Content from this work may be used under the terms of the Creative Commons Attribution 3.0 licence . Any further distribution of this work must maintain attribution to the author(s) and the title of the work, journal citation and DOI.
- Cloud Native Security
- Data Detection and Response
- Cloud Data Security &...
Cloud Data Security & Protection: Everything You Need to Know
Data is currency for modern businesses. Organizations use data analytics to make decisions about new products and services or to provide better customer experiences. As companies collect, store, transmit, process, and use more data, they increase their use of the cloud. Additionally, cloud-based technologies enable workforce collaboration across geographic regions as well as between internal and external users.
Complex IT environments often use a combination of on-premises, cloud, multicloud, and hybrid infrastructures, meaning that they store vast amounts of sensitive data in multiple locations. Often, organizations lose visibility into where sensitive data resides, who uses it, and whether it remains protected. In response, malicious actors have turned their attention to the cloud, looking to steal sensitive corporate and personally identifiable information (PII).
With an estimated 60% of enterprise data stored in the cloud, understanding cloud data security is fundamental to mitigating data breach, reputation, financial, and compliance risks.
Understanding Data Security
Data security includes the technologies and processes an organization uses to protect sensitive data both on-premises and in the cloud.
Sensitive information includes corporate and non-public personal information (NPI), including:
- Intellectual property
- Birth dates
- Government identification information, like social security numbers and driver's license information
- Physical address
- Biometric information
Further, as legislative bodies respond to ransomware attacks and data breaches by enacting new data protection laws, some best practices have emerged, including:
- Data classification
- Data anonymization and pseudonymization
- Data encryption
- User access controls
What Is Cloud Data Security?
Cloud data security refers to the technologies and controls that discover, classify, and protect all data in the cloud to mitigate risks arising from data loss, misuse, breaches, and unauthorized access. This includes:
- Detecting and classifying structured and unstructured data
- Implementing and monitoring access management controls at the file and field levels
- Identifying storage locations for structured and unstructured data
- Data transmission flows
- Encryption configurations
Data security is a fundamental component of an organization’s cybersecurity strategy.
Why Is Sensitive Data Protection Important in Cloud Computing?
As organizations use more data, they need to protect its confidentiality, integrity, and availability. Cloud computing models enable collaboration and analytics but present unique challenges.
Data Integrity
Cloud computing and analytics enable organizations to make data-driven decisions. According to the global IDC survey data :
- 83% of CEOs want a data-driven organization
- 74% of senior executives require data in decision making
Organizations need to protect sensitive information to ensure the integrity of the data that their analytics models use. To do this, they need to mitigate risks associated with unauthorized access, including internal users who can make changes to data.
Data Availability
As organizations build out their data cultures, breaking down data silos becomes more important. The cloud enables this collaboration, but organizations need to ensure that they protect sensitive information’s availability, like ensuring no one accidentally deletes a data set.
Data Confidentiality
With hybrid and multicloud environments, monitoring data use becomes even more challenging. As data travels between services, organizations need to worry about application programming interface (API) configurations. By protecting sensitive information, organizations prevent data loss and leaks that compromise confidentiality.
What Are the Benefits of Cloud Data Security?
While protecting sensitive data is important, the same practices, controls, and processes benefit companies, too.
Mitigate Data Breach Risk
Data security controls reduce a cyberattack’s success rate. For example, implementing data access controls makes it more difficult for attackers to get to the information. Other data controls, like encryption, make the data unusable and unreadable if attackers succeed.
Protect Brand Reputation
Brand reputation generates customer interest and provides insight into financial performance. The State of Corporate Reputation and Business Performance Report found that 72% of business leaders believe reputation will be a bigger driver of business performance than margin over the next five years. Every data breach that makes the news undermines a company’s brand reputation. By mitigating these risks, organizations protect themselves.
Enhance Customer Trust
Today’s customers consider a company’s data privacy policies and data protections as part of their buying decisions. Customer trust starts with an organization’s privacy policies, but it also incorporates brand reputation.
According to McKinsey , consumers want companies to provide transparency around digital-trust policies finding:
- 85% of respondents said knowing a company’s data privacy policies is important before making a purchase
- 46% of consumers often or always consider another brand if they are unclear about how a company will use their data
- 53% of consumers make online purchases or use digital services only after making sure that the company has a reputation for protecting its customers’ data
Cloud data security enables organizations to implement data privacy controls that ensure safe customer data sharing.
Avoid Fines and Fees
Data privacy and protection law noncompliance leads to costly fines and legal fees. For example, a company that violates the General Data Protection Regulation (GDPR) can face fines up to €10 million, or 2% of its worldwide annual revenue. These fines apply to violations which may not be cybersecurity incidents. For example, one of the first GDPR fines was levied against a Portuguese hospital for allowing too many people to have too much access. Additionally, companies often face expensive lawsuits in a data breach’s aftermath.
Who Is Responsible for Cloud Data Security?
Most cloud service providers follow the shared responsibility model for cloud security. At a high level, the cloud provider is responsible for the security of the cloud while their customer remains responsible for the security of applications and data in the cloud.
Each service provider and “as-a-Service'' model defines the shared responsibility differently. However, customers are typically responsible for:
- Information and data
- Application logic and code
- Identity and access
- Platform resource configuration
Infrastructure as a service (IaaS) and platform as a service (PaaS) implementations assign each party additional responsibilities, and these are dictated by the contract.
6 Cloud Data Security Challenges
For every benefit that cloud environments provide, they add a data security challenge. Cloud environments are inherently code-based, creating different risks.
Expanded Attack Surface
Cloud environments are naturally flexible and scalable, meaning that organizations can add new applications or workloads easily. Often, people deploy cloud assets outside of the organization’s security policies, creating misconfiguration risks. Further, IT and security teams may not know that these assets exist since traditional asset management tools lack real-time detection capabilities.
Complex Environments
Modern IT environments may include:
- One or more public cloud provider
- On-premises servers
- SaaS applications
- Virtual machines
As data travels between these assets, organizations find discovering all sensitive data and mapping data flows challenging.
Virtual machines, containers, and cloud instances pose new and unique challenges. As IT environments add more layers of abstraction, data security protections evolve, requiring security teams to focus on discovering these assets and maintaining secure configurations.
Divergent Permissions
The majority of organizations have multicloud environments. Maintaining situational awareness and proper security practices poses a challenge because they lack data normalization across logs. Although vendors provide monitoring tools, each provider uses different field names and varies the number of fields in the logs. Without data normalization in a centralized location, organizations struggle to gain visibility across disparate:
- Permissions
- Log formats
- Network configurations
Dynamic Environment
IT departments can create and delete volumes of cloud assets rapidly. While the cloud’s flexibility and scalability enables organizations to save money, consistently applying security policies becomes difficult. Security tools built for traditional environments lack real-time policy enforcement capabilities. Cloud asset configurations can fall out of compliance, weakening the organization’s data security posture.
Shadow Data
As engineering teams leverage cloud database technologies, they duplicate data. For example, they may have DB backups generated with sensitive information that were moved to the cloud and never deleted. Since most tools fail to discover this data, organizations are left with shadow data that can lead to a data breach.
Regulatory Compliance
Implementing data security controls is challenging. All the same, increased regulatory focus on data privacy means that organizations have to maintain their data security posture and document their activities. Inconsistent access permissions, configuration drift, and visibility issues lead to compliance violations and audit failures.
Best Practices for Implementing Cloud Data Security
By following best practices for data detection and classification, you can implement controls and technologies that help secure data.
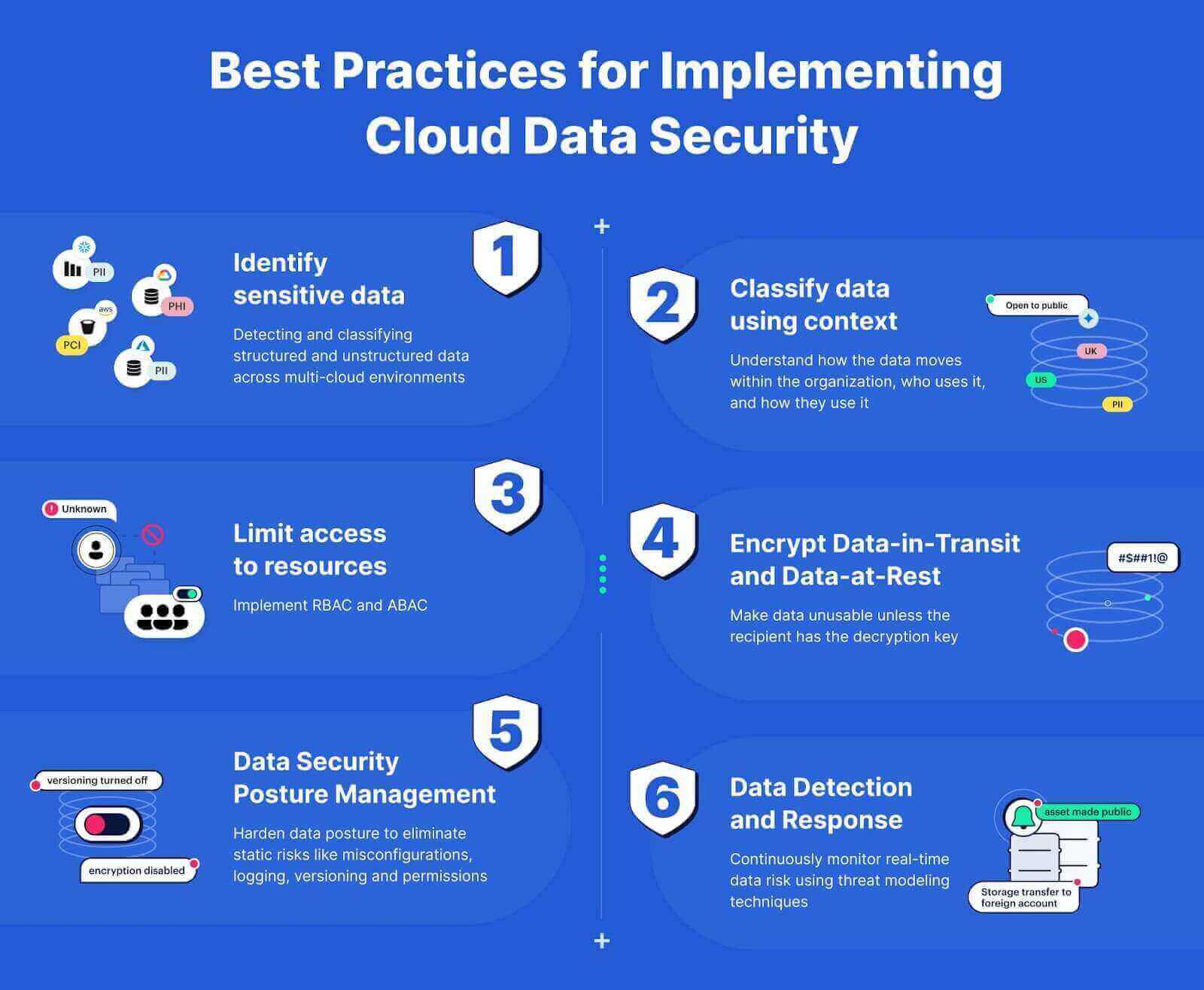
Identify Sensitive Data
Before you can secure data, you need to identify what sensitive information you have and where it resides. To gain visibility into critical data and static data risk, you need to discover and classify structured and unstructured sensitive data across:
- Public cloud platforms, including storage like S3 buckets, RDS, and EFS
- Virtualization environments
- Data analytics platforms, like Redshift
- Databases as a Service, like Snowflake
- Shadow data
Classify Data Using Context
Once you know where sensitive data resides, you need to classify it according to:
- Sensitivity level
- Governing regulation
Your classification process should include how the data moves within your organization, who uses it, and how they use it.
Limit Access to Resources
With all your data identified and classified, you can set user access permissions. You should limit access as precisely as possible, granting each user the least amount of access necessary to complete their job function. You should use a combination of:
- Role-based access controls (RBAC) : permissions assigned to someone based on their role in the organization, like job function or department
- Attribute-based access controls (ABAC) : permissions that incorporate context, like user device security, geographic location, or time of day
Encrypt Data-in-Transit and Data-at-Rest
Nearly every compliance mandate requires organizations to encrypt data-at-rest and in-transit . Encryption makes data unusable unless the recipient has the decryption key. If someone gains unauthorized access to it, they won’t be able to read it.
Implement Data Loss Prevention (DLP)
As users collaborate, you can experience data leakage or loss, meaning that someone shares data outside the organization when they shouldn’t have. Data loss can be a result of:
- Accidental sharing during collaboration
- Threat actors compromising systems and networks to steal data
- Malicious insiders downloading information
You should look for DLP solutions that implement near real-time data risk detection across multicloud environments as information travels between clouds and applications.
Harden Data Posture
As people use data, you need visibility into how they access different datasets so that you understand the evolving nature of data flows.
You can use data security posture management (DSPM) to identify static risks like:
- Misconfigurations, including disabled logging
- Encryption being disabled
- Versioning issues
Continuously Monitor Real-Time Data Risk
Since cloud environments are dynamic, your data risk posture continuously changes.
Additionally, you need to use threat modeling and threat intelligence for real-time risk detection that includes:
- Newly created data assets
- Newly discovered threats
- New attack methodologies impacting your cloud services providers
Create a Single Source for Continuous Monitoring, Remediation, and Documentation
For comprehensive visibility that documents your data security posture, you should aggregate all monitoring and remediation in a single location. With a comprehensive data security posture management (DSPM) and data detection and response (DDR) platform, you gain:
- A data-centric view of your cloud data assets , including content, identities and access, and data vulnerabilities and exposures
- Alerts that prioritize risk based on real-world attack methods for visibility into exploitability
- Automated remediation of data access violations connected to business workflows
- Audit documentation based on cloud, geographic region, and compliance standard
Learn More: Cloud Data Security
While complex and challenging, securing data stored in the cloud is critical. To remain competitive, companies need to use cloud technologies. But they need to mitigate data breach risks to protect brand reputation, customer loyalty, and financial stability.
Leveraging technologies that move at the speed of the cloud, enhance security while reducing the operational burdens that IT and security teams face. Prisma Cloud is the first vendor offering both data security posture management (DSPM) with data detection and response (DDR) capabilities to meet today’s organizations’ needs around multicloud data security. Our ability to improve existing security controls is a game changer in reducing the impact of data breach .
Don't miss the insights from the State of Cloud Data Security 2023 report . Uncover key findings from our analysis of over 13 billion files and 8 petabytes of data stored in public cloud environments.
Related Blogs
Data detection and response , data security , data security posture management , dlp, data security platforms: 9 key capabilities and evaluation criteria, data detection and response , data security , data security posture management, shadow data is inevitable, but security risks aren’t, an introduction to data detection and response (ddr), data detection and response , data security posture management , dlp , incident response, an incident response framework for cloud data security, cloud security posture management , data detection and response , data security, achieving cloud data and compliance: how you can make it work, data detection and response , data loss prevention , data security posture management, 5 essential components of a cloud dlp solution, subscribe to cloud native security blogs.
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement . Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.
Get the latest news, invites to events, and threat alerts
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement .
- USA (ENGLISH)
- AUSTRALIA (ENGLISH)
- BRAZIL (PORTUGUÉS)
- CANADA (ENGLISH)
- CHINA (简体中文)
- FRANCE (FRANÇAIS)
- GERMANY (DEUTSCH)
- INDIA (ENGLISH)
- ITALY (ITALIANO)
- JAPAN (日本語)
- KOREA (한국어)
- LATIN AMERICA (ESPAÑOL)
- MEXICO (ESPAÑOL)
- SINGAPORE (ENGLISH)
- SPAIN (ESPAÑOL)
- TAIWAN (繁體中文)
- UK (ENGLISH)
Popular Resources
- communities
- Content Library
- Event Center
- Products A-Z
Legal Notices
- Trust Center
- Terms of Use
Popular Links
- Manage Email Preferences
- Product Certifications
- Report a Vulnerability
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Comput Intell Neurosci
- v.2021; 2021

This article has been retracted.
Security and privacy risk assessment of energy big data in cloud environment.
1 Shenyang University of Technology, Shenyang, China
Yuanyuan Zhang
2 Dalian Medical University, Dalian, China
Associated Data
The data used to support the findings of this study are available from the corresponding author upon request.
Considering the importance of energy in our lives and its impact on other critical infrastructures, this paper starts from the whole life cycle of big data and divides the security and privacy risk factors of energy big data into five stages: data collection, data transmission, data storage, data use, and data destruction. Integrating into the consideration of cloud environment, this paper fully analyzes the risk factors of each stage and establishes a risk assessment index system for the security and privacy of energy big data. According to the different degrees of risk impact, AHP method is used to give indexes weights, genetic algorithm is used to optimize the initial weights and thresholds of BP neural network, and then the optimized weights and thresholds are given to BP neural network, and the evaluation samples in the database are used to train it. Then, the trained model is used to evaluate a case to verify the applicability of the model.

1. Introduction
In the era of big data, the application of big data technology in the energy field is a trend to promote industrial development and innovation. Both the deep application of big data technology in the energy field and the deep integration of energy production, consumption, and related technology revolution with big data concept will accelerate the development of energy industry [ 1 ].
With the implementation of the global energy big data strategy, the rapid development of “Internet plus” smart energy and the comprehensive construction of intelligent energy layout make the energy industry more widely distributed, more data collection points, more data types, more complex business relationships, and a wider range of data usage and users [ 2 ]. So while bringing convenience, it also brings risks to energy big data management. Due to the critical infrastructure of each country, energy is bound to become the preferred target of attack in case of cyber war. With the frequent occurrence of more and more energy security and privacy incidents, such as “Blackout in Ukraine” and “Stuxnet virus” attack on Iran's nuclear facilities, big data has become a usable and attachable carrier [ 3 ]. Through the big data value information obtained by the attack, the energy distribution of the target location can be analyzed, and the key data such as the monitoring and early warning information and operation instructions of key nodes will be tampered, resulting in energy system failure or major security accidents.
Therefore, the management research based on energy big data has been widely concerned by scholars all over the world. At present, for the huge amount of data and the particularity of management in the energy industry, scholars carry out data management and architecture design through various technical or nontechnical means, including the establishment of big data layer to store and process renewable energy data [ 4 ] and the establishment of energy big data processing system, supporting memory distributed computing [ 5 ]. In the research on the security and privacy of big data, it is found that most scholars used a single model for risk assessment, such as analytic hierarchy process (AHP), factor analysis, grey theory [ 6 ], fuzzy evaluation method [ 7 ], and cloud model [ 8 ]. Such methods are based on statistical theory and cannot completely get rid of the influence of subjectivity and theoretical assumptions. In recent years, machine learning has become an important research tool in the field of security and privacy [ 9 ]. When using machine learning methods to evaluate and predict risks, the accuracy is often higher than that of traditional statistical methods [ 10 ]. Common machine learning methods include neural network, SVM, and clustering algorithm; BP neural network is the most widely used neural network in risk prediction and evaluation [ 11 ], but which is easy to fall into local minimum in practical application [ 12 ]. Therefore, scholars often use other algorithms as assistance to improve the accuracy of prediction and evaluation. For example, Zhang (2021) established a regression model through BP network and used PSO algorithm to optimize connection weights to evaluate the slow convergence of BP network, in order to improve the accuracy of rockburst prediction [ 13 ]. Wang (2019) et al. used LM algorithm to improve the operation efficiency and accuracy of traditional BP neural network and provided an effective theoretical basis and modeling method for risk prediction of power communication network [ 14 ].
This greatly improves the accuracy of prediction and evaluation, but a review of the relevant literature shows that the analysis of the importance of the impact of indexes is often neglected. Thus, in this paper, based on the consideration of machine learning, according to the different degrees of risk impact, AHP method is used to determine the index weight, which overcomes the deficiency of subjective consideration in previous studies [ 15 ]; the genetic algorithm optimized BP neural network (hereinafter referred to as GABP) with better prediction and evaluation effect is used for evaluation [ 16 ], which is a successful attempt to realize the combination of energy field and deep learning. In addition, for the security and privacy risk assessment of energy big data, the current literature pays more attention to theoretical analysis and lacks a relatively perfect assessment reference system. Starting from the whole life cycle of big data and considering the cloud environment, this paper establishes a risk assessment index system of energy big data security and privacy, which enriches the theoretical basis and framework in this field to a certain extent.
2. The Index System of Security and Privacy Risk Assessment of Energy Big Data in Cloud Environment
2.1. principles for the construction of the index system.
In the process of risk assessment, the probability of risk occurrence, loss range, and other factors need to be considered comprehensively to get the possibility and degree of system risk occurrence, determine the risk level, and then decide whether to take corresponding control measures and to what extent [ 17 ].
Therefore, the construction of risk assessment index system should follow the principles of comprehensiveness, scientificity, representativeness, and practicability, select the representative risk elements from a scientific perspective, quantify the risk based on the practical principle, and strive to show the risk management level comprehensively and accurately.
2.2. Identification of Risk Factors
Data security management is the most prominent risk faced by big data application. Although the massive data is stored centrally, it is convenient for data analysis and processing, but the loss and damage of big data caused by improper security management will cause devastating disaster. Due to the development of new technology and new business, the infringement of privacy right is not limited to physical and compulsory invasion, but is derived in a subtler way through various data, and the data security and privacy risks caused by this will be more serious [ 18 ].
Compared with the previous Internet and computer technology, the application advantage of big data in the cloud environment is more obvious. Big data platform has strong sharing ability, which can manage the security of information use and improve the efficiency of resource utilization. The construction of cloud platform and system application have strict standards. Cloud computing technology provides more comprehensive technical support and makes privacy management more reasonable, which is consistent with the level of technology development in the new era [ 19 ]. But from another point of view, it is under the influence of cloud platform sharing features that part of the data information is easy to be exposed, which provides opportunities for some illegal intrusion. Therefore, we must pay full attention to its risks.
Based on the literature of Xu [ 20 ], Tawalbeh [ 21 ], and He [ 22 ], combined with the analysis of relevant cases and the consultation of professionals, this paper follows the above evaluation index setting principle, combines with the development characteristics of energy big data security factors, and considers the impact of cloud environment. From the perspective of the whole life cycle of big data, this paper summarizes the current privacy security risks of cloud computing and big data and divides the risk assessment factors into five stages: data collection, data transmission, data storage, data use, and data destruction, with a total of 22 indexes, as shown in Figure 1 .

Security and privacy risk assessment index system based on the whole life cycle of energy big data.
2.3. Index Quantification
In terms of data collection, for the quantification of energy big data security and privacy risk indexes, this study introduces the concept of risk degree. According to the occurrence possibility and loss degree of each risk index, the product of possibility and loss degree is used as the reference standard of risk degree quantification, and the specific value can be reasonably floating around the product. The quantification of probability and loss degree can be divided into five levels: very high risk (5 points), high risk (4 points), medium risk (3 points), low risk (2 points), and very low risk (1 point).
In formula ( 1 ), P is the probability of occurrence and L is the degree of loss.
The normalized input value is multiplied by the corresponding weight of each index as the input of the neural network for training, combined with the output value; the risk assessment level can be obtained, as shown in Table 1 .
Risk assessment level.
3. Assessment Model of Energy Big Data Security and Privacy Risk in Cloud Environment
3.1. ahp method.
In the existing BP neural network part of the process, all kinds of risk factors are default to the same degree of impact, without a rigorous distinction, which is adverse to the establishment of neural network model.
Considering the particularity of energy big data security and privacy risk, quantitative analysis method may not be able to reasonably determine the real impact degree of indexes. Therefore, AHP method is used to give weight to indexes in this paper, and various factors in complex problems are divided into interconnected and ordered levels to make them methodical. According to the subjective judgment structure of certain objective reality, the expert opinions and the objective judgment results of analysts are directly and effectively combined, and the importance of pairwise comparison of one level elements is quantitatively described.
Therefore, after the establishment of energy big data security privacy and risk assessment index system, according to the influence degree of each risk factors, the Delphi method is used to invite experts to quantify the importance between them, and the AHP method is used to give corresponding weights to 22 indexes.
- (1) Construct the judgment matrix.
Scale specification.
- (2) Calculate the eigenvalue and eigenvector by the square root method and calculate the product of elements in each row of judgment matrix. M i = ∏ j = 1 n a i j i = 1,2 , … , n . (2)
- Calculate the n th root of M i . W i ¯ = M i n i = 1,2 , … , n . (3)
- Normalize the eigenvectors as the weight. W A = W 1 , W 2 , … , W n T . (4)
- Calculate the largest eigenvalue, where (AW) i is the i th component of the vector AW. λ max = ∑ i = 1 n AW i n W i . (5)
- (3) Check for consistency.
The consistency index C.I. is
Generally, C . I .≤0.10 represents that the judgment matrix is consistent.
Obviously, with the increase of value n , the judgment error will increase, so the influence of n should be considered when judging the consistency, and the random consistency ratio C . R .= C . I ./ R . I . should be used, where R.I. is the average random consistency index. Table 3 shows the average random consistency index test values calculated by the judgment matrix.
R.I. value.
3.2. BP Neural Network
BP neural network is a kind of multilayer neural network, which was proposed by Rumelhart in 1986. It is one of the most widely used neural network models at present. It can learn and store a large number of input-output pattern mapping relations. Its learning rule is to use the steepest descent method to continuously adjust the weights and thresholds of the network through back propagation, so as to minimize the mean squared errors of the network. It is usually composed of input layer, hidden layer, and output layer [ 23 ], and its network model is shown in Figure 2 .

Structural model of neural network.
The basic unit of neural network is neuron. The principle formula is shown in formula ( 7 ); the commonly used activation functions are threshold function, sigmoid function, and hyperbolic tangent function. In formula ( 7 ), the input of neurons is represented by x i ( i = 1, 2,…, n ), the connection weights between neurons are represented by w i ( i = 1, 2,…, n ), the threshold of neurons is b , the activation function is f , and the output of neurons is y .
For BP neural network, the mean square error E is often used as the index to judge the training performance of the model, shown in formula ( 8 ). The principle of minimizing the mean square error by adjusting the network weights is shown in formula ( 9 ), where e is the network error vector, y i is the model output, and t i is the target output.
For the training model, the LM algorithm of neural network is used in this study. The basic method to reduce the error is as follows:
where H is the Jacobi matrix of the first derivative of the MSE function with respect to weights and thresholds.
3.3. Genetic Algorithm
Genetic algorithm (GA) is a computational model simulating the natural selection and genetic mechanism of Darwinian biological evolution theory. It is a method to search the optimal solution by simulating the natural evolution process [ 24 ].
Using genetic algorithm to get the optimal network weights and thresholds as the initial network weights and thresholds of the subsequent neural network model can not only overcome the defect that the traditional BP neural network is easy to fall into the local minimum, but also greatly improve the accuracy of model evaluation, so that the optimized BP neural network can better evaluate the samples. The elements of genetic algorithm include population initialization, fitness function, selection operator, crossover operator, and mutation operator.
Compared with binary coding, real coding can significantly reduce the length of coding and avoid the later decoding, with high accuracy. A series of parameters to be optimized, such as the connection weight, hidden layer node threshold, and output layer node threshold, are encoded by the s-order real matrix with the value range of [−1, 1].
After coding, the selection, crossover, and mutation are performed. These three operations are based on the fitness value calculated by the fitness function as the assessment standard. The smaller the value, the larger the fitness value, and the better the individual. The fitness function of this study is the reciprocal of mean square error function, as follows:
In the selection operation, the most common roulette method is used. The probability of each individual being selected is positively proportional to its fitness value. N represents the population size, F i represents the fitness function value of individual i , and p i represents the probability of the i th individual being selected. The calculation way is as follows:
By using arithmetic crossover as formula ( 13 ), a new individual is obtained by using the linear combination between two individuals, where d is a random number uniformly distributed in [0, 1]:
Mutation operation refers to the random mutation of individual gene of the population, enhancing the local search ability of the algorithm and maintaining the diversity of individual population. The operation method of mutation of the j gene of the i individual a ij is as follows:
where a max is the upper bound of gene a ij , a min is the lower bound of gene a ij f ( g )= r 2 (1 − g / G max ) 2 , r 2 is a random number, g is the current iteration number, G max is the maximum evolution number, and r is the random number of [0, 1] interval.
3.4. Construction of AHP-GABP Model
Compared with the traditional BP neural network, GABP model has a process of using genetic algorithm to optimize the weights and thresholds of the network, and this process can optimize the prediction performance of BP neural network to a certain extent. At the same time, using the AHP method to confirm the indicator weights can better define the importance of indicators. The flowchart is shown in Figure 3 . The steps to build the AHP-GABP model are as follows:
- Use AHP method to process data.
- Determine the topological structure of BP neural network.
- After the weights are given by AHP, determine the input and output sample set and test sample set of training.
- The network parameters to be optimized are real-coded to form their own chromosomes.
- Determine the parameters of selection, crossover, and mutation.
- Set the population size popu.
- After inputting samples, each chromosome produces corresponding output after network transmission.
- The fitness value of each chromosome is calculated by fitness function, and the selection operation is carried out according to the fitness value.
- A new generation of population is generated by crossover and mutation.
- Repeat steps 6–8 until the fitness value of the optimal individual and the fitness value of the population do not rise within the specified number interval, or the fitness value of the optimal individual reaches the set threshold, or the number of iterations reaches the algebra set in advance, the algorithm stops, and the optimized network parameters are obtained.

AHP-GABP flowchart.
4. Evaluation Process
4.1. model training, 4.1.1. network design.
(1) Network Structure Determination . The paper selects 22 assessment indexes to assess the security and privacy risk of energy big data, so the number of input layer nodes is 22. In general, if the number of hidden layers is more, the error of assessment results will be smaller, but it will also bring the disadvantages of network complexity, thus reducing the efficiency of training [ 25 ]. For the multi-input single-output network model established in this paper, in order to increase the approximation effect and convergence, and reduce the oscillation in the simulation process, the number of hidden layer nodes is determined by referring to equation ( 15 ) and combining with the actual simulation results.
where m represents the number of input layer nodes, n represents the number of output layer nodes, a takes a random integer between 1 and 10, and S 1 = 12 is determined after trial calculation. The final MATLAB structure is shown in Figure 4 .

MATLAB structure.
(2) Parameter Setting . This study uses feedforward net to create function, trainlm to train function, logsig to transfer function, sigmoid to activate function, and MSE to express error E. The training times is 100, the learning rate is 0.01, and the training error target is 0.01. For the part of genetic algorithm, the number of population is set to 100, the maximum evolution algebra is set to 100, the variable precision is 1 e − 6, the crossover probability is 0.8, and the mutation probability is 0.2.
4.1.2. Training Results
After reading the literature and cases about the security and privacy risk of energy big data, a total of 44 samples are collected, including 36 training samples and 8 test samples. Some of the training data are shown in Table 4 . The model training is realized by MATLAB programming and the development of Goat genetic algorithm toolbox.
Training samples.
The training data is input into the program, and the convergence curve of genetic algorithm optimized BP neural network is shown in Figure 5 . It can be seen from the figure that the BP neural network algorithm after genetic algorithm optimization finds an optimal path optimal solution when the population iteration is about 60 generations, which shows the superiority of genetic algorithm in optimizing the weight and threshold of BP neural network. It can also be seen that the optimal function tends to be stable when the iteration reaches nearly 70 generations.

Fitness value.
The BP neural network and the optimized genetic BP neural network are compared, and their error values are calculated. The final experimental results are shown in Table 5 . Through analysis and comparison, in 8 groups of test samples, AHP-GABP prediction has significant advantages over BP prediction, with smaller error, shorter evaluation cycle, and greater improvement in evaluation performance. As shown in Table 5 and Figure 6 , the BP neural network optimized by genetic algorithm improves the shortcomings of BP neural network, thus greatly improving the predictability of neural network. At the same time, the application assessment results of the BP neural network optimized by genetic algorithm in the energy big data security and privacy risk are basically consistent with the actual expert assessment results, which proves that the training network has high accuracy.

Error comparison between predictive value and real value.
Comparison of training sample error between BP neural network and AHP-GABP neural network.
4.2. Model Applications
4.2.1. background.
Z power grid system uses its energy big data information to provide data services related to economic development. It can provide more reliable data support for poverty alleviation effect evaluation, credit evaluation, census, pollution monitoring, and work resumption evaluation. According to the energy big data security and privacy risk assessment index system designed above, the complete evaluation steps of big data security and privacy risk of this power grid system are as follows:
- Calculate the index weights using AHP method.
- Collect relevant data of this grid system, invite relevant department heads to score the 22 risk assessment indicators, and standardize the data with the weights as the input values of the AHP-GABP model.
- Use the above trained AHP-GABP network model; the output values are evaluated, and the risk level is defined according to the risk classification method.
4.2.2. Initial Index Weight of AHP Method
In this study, AHP method is used to assign weights to the primary and secondary indexes, respectively. After the consistency check, the final weights of 22 indexes are obtained as shown in Table 6 .
Weights of risk assessment indexes.
4.2.3. Assessment Results
In this study, three groups of relevant data collected by the power grid system are selected. After training, the AHP-GABP neural network model is established. Firstly, it is necessary to verify whether the evaluation model is reasonable. Secondly, it is necessary to assess the risk. The assessment results are shown in Table 7 , which shows that the risk level of the power grid system is class 1, which is similar to the conventional risk performance of the power grid system. The risk level is low, and there is no need to do special treatment, and regular inspection should be done. It also shows that the AHP-GABP algorithm is reasonable and correct in the evaluation and prediction, with high prediction accuracy, objective and fair evaluation results, wide application range, and high practical application value.
Case assessment result.
5. Conclusion and Development Suggestions
To sum up, in the process of controlling the energy big data security and privacy risk, the risk of each stage cannot be ignored. On the premise of comprehensively considering the cloud environment and risk factors, this paper divides the potential energy big data security and privacy risk of each stage as comprehensively as possible according to the life cycle of big data, and uses AHP method to allocate weights for the indexes, which provides a reference for the future energy big data research. At the same time, this paper optimizes the BP neural network model based on the evaluation, and tries to apply the AHP-GABP method to the risk evaluation of energy big data security and privacy, which greatly reduces the risk that the random selection of initial weights and thresholds in BP algorithm leads to the model training easily falling into the local minimum, and improves the accuracy of neural network model assessment and predication and realizes the application of AI related knowledge in the field of energy.
The AHP-GABP model is applied to evaluate the security and privacy of the energy big data, and the evaluation results are good. According to the case and expert interviews, the following development suggestions are summarized for the common risks of energy big data security and privacy.
5.1. Pay Attention to the Security of the Whole Life Cycle of Energy Big Data
Energy big data comes from production data and operation and management data, and its protection should focus on the whole life cycle of data collection, transmission, storage, use, and destruction. From policy and system requirements to technical management and control, we should comprehensively assess the threat exposure of critical data and make targeted protection strategies at all stages to ensure the security of core data assets.
5.2. Strengthen Technical Protection of Energy Industry Based on Big Data Security
The energy industry should establish a comprehensive threat early warning technology based on security big data, break through the traditional mode, and more actively detect potential security threats. The introduction of big data analysis technology in threat detection can more comprehensively detect attacks on data assets, software assets, physical assets, personnel assets, service assets, and other intangible assets supporting business [ 26 ]. At the same time, the scope of the analysis content can be expanded. The threat analysis window can span several years of data, so the threat detection ability is stronger and can effectively respond to the attack [ 27 ].
5.3. Consider Security and Privacy Issues from a Strategic and Long-Term Perspective
Big data brings opportunities and challenges to the energy industry. The more widely it is applied, the greater the value it brings. The concept of security management centered on data security will change the traditional working ideas [ 28 ]. We must recognize the new changes, new features, and new trends of big data security, and deeply analyze the outstanding problems existing in big data security under the current situation. In order to ensure that the development strategy of energy big data information security is consistent with the national conditions and constantly improves, it is necessary to plan the key layout of big data application, key technology research and development, data protection, laws and regulations.
With the rapid development of cloud computing and the continuous improvement of digital level, the energy big data security and privacy risk evaluation index system can be further improved. At the same time, with the enrichment of data indicators and training models, the model proposed in this paper can also be better optimized and expanded to other fields for more accurate evaluation and prediction in the future.
Acknowledgments
This work was financially supported by the Liaoning Planning Office of Philosophy and Social Science Project L19BXW006.
Data Availability
Conflicts of interest.
The authors declare that they have no conflicts of interest regarding the publication of this paper.
A Comparative Study on Cyber security Technology in Big data Cloud Computing Environment
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Frontiers in Big Data
- Data Mining and Management
- Research Topics
Big Scientific Data Analytics on HPC and Cloud
Total Downloads
Total Views and Downloads
About this Research Topic
Scientific studies in many science and engineering disciplines such as atmospheric science and health are becoming a major source of generating big data including simulation and observational data. At the same time, more and more scientific studies are utilizing big data analytics (including machine/deep ...
Keywords : Big Data Analytics, HPC, Cloud, Scalable data processing, Scalable machine learning, Reproducible big data, High-speed stream, GPU acceleration
Important Note : All contributions to this Research Topic must be within the scope of the section and journal to which they are submitted, as defined in their mission statements. Frontiers reserves the right to guide an out-of-scope manuscript to a more suitable section or journal at any stage of peer review.
Topic Editors
Topic coordinators, recent articles, submission deadlines.
Submission closed.
Participating Journals
Total views.
- Demographics
No records found
total views article views downloads topic views
Top countries
Top referring sites, about frontiers research topics.
With their unique mixes of varied contributions from Original Research to Review Articles, Research Topics unify the most influential researchers, the latest key findings and historical advances in a hot research area! Find out more on how to host your own Frontiers Research Topic or contribute to one as an author.
A Unified Approach Toward Security Audit and Compliance in Cloud Computing
- REVIEW PAPER
- Published: 23 March 2024
Cite this article
- Y. S. Rajesh 1 , 2 ,
- V. G. Kiran Kumar ORCID: orcid.org/0000-0001-9347-3867 3 &
- Asmita Poojari ORCID: orcid.org/0000-0003-2994-1958 4
15 Accesses
Explore all metrics
The use of cloud computing has become a reliable information technology solution over the past decade by providing numerous services and resources on a pay-as-you-use basis and evolving from concept to reality. Despite increasing demand and popularity, the adoption of the cloud is hindered mainly by security concerns. Successful cloud adoption and uncomplicated operation are possible if users, intermediaries, and service providers act reliably according to regulations by assuring shared responsibility policy. The biggest challenge in the audit and assurance of cloud computing is the lack of a de facto approach to meet an enterprise’s requirements. The primary focus is on the challenges and effectiveness of audit and assurance by conducting an exploratory study on industry best practices, auditing standards, required certifications, and regulatory compliance frameworks like GDPR, Sarbanes–Oxley, ENISA, ISO 27001, NIST, EU-SEC, OWASP, BSI C5, CIS, ANSSI, HIPAA, CCM, CSA STAR, PCI DSS, COBIT, and SOC in a cloud environment and classifying on basis of applicability. In this research paper, we provide general guidelines on auditing standards by referring to threads and vulnerabilities analyzed and suggesting a unified approach toward audit considerations in cloud computing environments.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

Cloud Security Auditing: Major Approaches and Existing Challenges

Cloud Computing Security Requirements and a Methodology for Their Auditing

Top Threats to Cloud: A Three-Dimensional Model of Cloud Security Assurance
Availability of data and material.
No such data were used.
H.A.S. Ahmed, M.H. Ali, L.M. Kadhum, M.F. Zolkipli, Y.A. Alsariera, A review of challenges and security risks of cloud computing. J. Telecommun. Electron. Comput. Eng. 9 (1–2), 87–91 (2017)
Google Scholar
A.R. Alobaidi, Z.N. Nuimi, Cloud computing security based on OWASP. 2022 5th International Conference on Computing and Informatics (ICCI) (2022), p. 22–28
M. Anisetti, C.A. Ardagna, E. Damiani, F. Gaudenzi, A security benchmark for openstack. 2017 IEEE 10th International Conference on Cloud Computing (CLOUD) (2017), p. 294–301
M. Moghadasi, S. Majid, G. Fazekas, Cloud computing auditing roadmap and process. Int. J. Adv. Comput. Sci. Appl. 9 (2018). https://doi.org/10.14569/IJACSA.2018.091265
R. Kumar, R. Goyal, On cloud security requirements, threats, vulnerabilities and countermeasures: a survey. Comput. Sci. Rev. 33 , 1–48 (2019). https://doi.org/10.1016/j.cosrev.2019.05.002
U.M. Ismail, S. Islam, A unified framework for cloud security transparency and audit. J. Inf. Secur. Appl. 54 , 102594 (2020)
G. Mateescu, V. Sgârciu, Cloud computing audit. Sci. Bull. UPB Ser. C: Electr. Eng. 77 (3) (2015)
N. Carter, Auditing the ISO 19011 Way (BSI British Standards Institution, 2003)
J. Ryoo, S. Rizvi, W. Aiken, J. Kissell, Cloud security auditing: challenges and emerging approaches. IEEE Secur. Priv. 12 (6), 68–74 (2014). https://doi.org/10.1109/MSP.2013.132
Article Google Scholar
X. Kontargyris, IT Laws in the Era of Cloud-Computing: A Comparative Analysis between EU and US Law on the Case Study of Data Protection and Privacy (Nomos) (Schriften der Albrecht Mendelssohn Bartholdy Graduate School of Law, 2018)
D. Yimam, E.B. Fernandez, A survey of compliance issues in cloud computing. J. Internet Serv. Appl. 7 (1), 1–12 (2016)
S. Karkosková, Towards cloud computing management model based on ITIL processes. in Proceedings of the 2nd International Conference on Business and Information Management (2018)
N. Cook, D. Milojicic, V. Talwar, Cloud management. J. Internet Serv. Appl. 3 (1), 67–75 (2012)
T. Forell, D. Milojicic, V. Talwar, Cloud management: challenges and opportunities. 2011 IEEE International Symposium on Parallel and Distributed Processing Workshops and Phd Forum (2011), p. 881–889
S. Ismaeel, A. Miri, D. Chourishi, S.M.R. Dibaj, Open source cloud management platforms: a review. 2015 IEEE 2nd International Conference on Cyber Security and Cloud Computing (2015), p. 470–475
M. Niranjanamurthy, M.P. Amulya, N.M. Niveditha, P. Dayananda, Creating a custom virtual private cloud and launch an Elastic Compute Cloud (EC2) instance in your virtual private cloud. J. Comput. Theor. Nanosci. (American Scientific publishers), 17 (15), 4565–4570 (2020). https://doi.org/10.1166/jctn.2020.9106
R. Los, D. Shackleford, B. Sullivan, The notorious nine cloud computing top threats in 2013. Cloud Secur. Alliance, 2 (2013)
S.O. Kuyoro, F. Ibikunle, O. Awodele, Cloud computing security issues and challenges. Int. J. Comput. Netw. 3 (5), 247–255 (2011)
A. Dutta, G.C.A. Peng, A. Choudhary, Risks in enterprise cloud computing: the perspective of IT experts. J. Comput. Inf. Syst. 53 (4), 39–48 (2013)
N. Tissir, S. el Kafhali, N. Aboutabit, Cybersecurity management in cloud computing: semantic literature review and conceptual framework proposal. J. Reliab. Intell. Environ. 7 (2), 69–84 (2021)
M. Chiregi, N. Jafari Navimipour, Cloud computing and trust evaluation: a systematic literature review of the state-of-the-art mechanisms. J. Electr. Syst. Inf. Technol. (2018)
T. Rübsamen, Evidence-Based Accountability Audits for Cloud Computing. (Doctoral Dissertation, University of Plymouth, 2016)
F. Simetinger, Audit and assurance specifics in cloud-based industry 4.0 environment. J. Syst. Integr. 9 (3), 7–17 (2018). https://doi.org/10.20470/jsi.v9i3.349
L. M. Brumă, “Cloud security audit – issues and challenges,” 2021 16th International Conference on Computer Science & Education (ICCSE), Lancaster, United Kingdom, pp. 263–266 (2021). https://doi.org/10.1109/ICCSE51940.2021.9569654
U.M. Ismail, S. Islam, H. Mouratidis, Cloud Security Audit for Migration and Continuous Monitoring. 2015 IEEE Trustcom/BigDataSE/ISPA, vol. 1 (2015), p. 1081–1087. https://doi.org/10.1109/Trustcom.2015.486
F. Doelitzscher, Security audit compliance for cloud computing. University of Plymouth 2014 Phd Thesis., PEARL (2014)
A. Nagar, K.P. Joshi, A semantically rich knowledge representation of PCI DSS for cloud services. 6th International IBM Cloud Academy Conference ICACON 2018, Japan (2018)
G. Ataya, PCI DSS audit and compliance. Inf. Secur. Tech. Rep. 15 (4), 138–144 (2010)
L. Elluri, K.P. Joshi, A knowledge representation of cloud data controls for EU GDPR compliance. 2018 IEEE World Congress on Services (SERVICES) (2018), p. 45–46
S. Islam, M. Ouedraogo, C. Kalloniatis, H. Mouratidis, S. Gritzalis, Assurance of security and privacy requirements for cloud deployment models. IEEE Trans. Cloud Comput. 6 (2), 387–400 (2018). https://doi.org/10.1109/TCC.2015.2511719
H.M. Melaku, Context-based and adaptive cybersecurity risk management framework. Risks (2023)
M. Barati, O. Rana, Checking GDPR compliance for cloud-based services. 2021 IEEE World Congress on Services (SERVICES) (2021), p. 2
D. Kim, K.P. Joshi, A semantically rich knowledge graph to automate hipaa regulations for cloud health it services. in 2021 7th IEEE Intl Conference on Big Data Security on Cloud (BigDataSecurity), IEEE Intl Conference on High Performance and Smart Computing (HPSC) and IEEE Intl Conference on Intelligent Data and Security (IDS) (2021), p. 7–12
M. Kelly, E. Furey, K. Curran, How to achieve compliance with gdpr article 17 in a hybrid cloud environment. Science 3 (1), 3 (2021)
C. Mitchell, Privacy, compliance and the cloud. Guide to Security Assurance for Cloud Computing (2015), p. 3–14
S. Okour, The impact of the application of IT governance according to (COBIT 5) framework in reduce cloud computing risks. Mod. Appl. Sci. 13 (7), 25 (2019)
P. Olajide, PCI DSS compliance validation of different levels of merchants in a multi-tenant private cloud (2013)
M. Piazza, J. Fernandes, J. Anderson, A. Olmsted, Cloud payment processing without ritualistic sacrifices reducing PCI-DSS risk surface with thin clients. 2016 International Conference on Information Society (i-Society) (2016), p. 166–168
C.E. Pugh, M. Hilley, Regulatory Compliance and Total Cost Influence on the Adoption of Cloud Technology: A Quantitative Study [Doctoral dissertation, Capella University]. In ProQuest Dissertations and Theses. (2021). https://www.proquest.com/dissertations-theses/regulatory-compliance-total-cost-influence-on/docview/2572572997/se-2
G.A. Reid, S. Miller, Improving HIPAA Compliance Efforts with Modern Cloud Technologies [(Doctoral dissertation, Capitol Technology University).]. In ProQuest Dissertations and Theses. (2021). https://www.proquest.com/dissertations-theses/improving-hipaa-compliance-efforts-with-modern/docview/2595993643/se-2?accountid=12118
C. Racuciu, S. Eftimie, Security threats and risks in cloud computing. Sci. Bull. Mircea Cel Batran Nav. Acad. 18 (1), 105 (2015)
R. Ahmad, Cloud Security and Governance. Metropolia University of Applied Sciences, Master’s Thesis (Information Technology), (2021)
S. Subashini, V. Kavitha, A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 34 (1), 1–11 (2011)
L. Schubert, Ustutt-Hlrs, K.G. Jeffery, B.K. Neidecker-Lutz, L. Schubert, E. Ustutt-Hlrs, A Roadmap for Advanced Cloud Technologies Under H 2020 Recommendations by the Cloud Expert Group (2012)
D. Wang, D. Zhong, L. Li, A Comprehensive Study of the Role of Cloud Computing on the Information Technology Infrastructure Library (ITIL) Processes (Library Hi Tech, 2021)
R. Wu, G.-J. Ahn, H. Hu, Towards HIPAA-compliant healthcare systems in cloud computing. Int. J. Comput. Models Algorithms Med. 3 (2), 1–22 (2012)
G. Weir, A. Aßmuth, M. Whittington, B. Duncan, Cloud accounting systems, the audit trail, forensics and the EU GDPR: how hard can it be? British Accounting & Finance Association (BAFA) Annual Conference 2017 (2017)
Download references
Acknowledgments
The authors would like to thank PSOM Technologies Private Limited, Bengaluru, India, the Department of Electronics and Communication and Engineering, A J Institute of Engineering and Technology, Department of Computer Science and Engineering, NMAMIT NITTE, and Upgrad Education Private Limited, Nishuvi, 75, Dr. Annie Besant Road, Worli, Mumbai, for the support for carrying out the research work
No funding.
Author information
Authors and affiliations.
MS UpGrad Education Private Limited, Nishuvi, 75, Dr. Annie Besant Road, Worli, Mumbai, 400018, India
Y. S. Rajesh
PSOM Technologies Pvt Ltd, Bengaluru, India
Department of Electronics and Communication Engineering, A J Institute of Engineering and Technology, Kottara-Mangalore, 575006, India
V. G. Kiran Kumar
Department of Computer Science and Engineering, N M A M Institute of Engineering and Technology, Karkala, India
Asmita Poojari
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to V. G. Kiran Kumar .
Ethics declarations
Conflicts of interest/competing interests.
The authors declare that they have no conflicts of interest.
Consent for Publication
Authors give consent for publication in the journal.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Rajesh, Y.S., Kumar, V.G.K. & Poojari, A. A Unified Approach Toward Security Audit and Compliance in Cloud Computing. J. Inst. Eng. India Ser. B (2024). https://doi.org/10.1007/s40031-024-01034-x
Download citation
Received : 15 March 2023
Accepted : 26 February 2024
Published : 23 March 2024
DOI : https://doi.org/10.1007/s40031-024-01034-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cloud computing
- Cloud security
- Security auditing
- Find a journal
- Publish with us
- Track your research

IMAGES
COMMENTS
In the big data cloud computing environment, data security issues have become a focus of attention. This paper delivers an overview of conceptions, characteristics and advanced technologies for big data cloud computing. Security issues of data quality and privacy control are elaborated pertaining to data access, data isolation, data integrity, data destruction, data transmission and data ...
It is the principle of big data analysis and processing technology that manages the data and provides pay-per-use service for users (F. Wang et al., 2021). Cloud data storage allows the user to ...
1. Introduction. Big Data in the cloud computing environment is built on the new network technology under the premise of network information technology. Using the virtualized network platform, users can store and process data, and can use the network to transmit data to users again. As a new form of data processing, big data security technology ...
As the amount of data is increasing day by day, cloud has become a perfect solution to store data by providing virtually unlimited storage that can be accessed over the Internet. By outsourcing large volume of data to cloud storage, such as Google Drive, Dropbox, and Amazon Simple Storage Service, users can simplify their data management and reduce data maintenance costs through the pay-as-you ...
The resource security problem of data in cloud computing system is essentially a data access control problem, which is mainly manifested in the illegal access of users to data. This threat includes two types, namely, internal threat and external threat. When a user applies big data technology to host the data to the cloud platform or store the ...
Cloud computing is an Internet-based technology that emerging rapidly in the last few years due to popular and demanded services required by various institutions, organizations, and individuals. structured, unstructured, semistructured data is transfer at a record pace on to the cloud server. These institutions, businesses, and organizations are shifting more and more increasing workloads on ...
In the epoch of digital technology, cloud computing, big data, fog computing, IoT, and blockchain computing are leading research domains. The authors have critically examined big data topics connected with blockchain, IoT, and m-health in this research article [169, 170]. The big-data architecture is decentralized and non-homogeneous.
These trends include cloud and mobile cloud computing but along with these technologies there are many associated challenges that should be taken in consideration such as users privacy and data security. In this research we studied the re- cent emerging technologies that include: cloud systems, mobile cloud computing, P2P cloud systems, big ...
Data integrity in the cloud system means preserving information integrity. The data should not be lost or modified by unauthorized users. Data integrity is the basis to provide cloud computing service such as SaaS, PaaS, and IaaS. Besides data storage of large-scaled data, cloud computing environment usually provides data processing service.
Therefore, the demand for data processing needs to be improved urgently, and Cloud computing and big data technology as the product of the development of computer networks came into being. However, the following data collection, storage, and the security and privacy issues in the process of use are faced with many risks.
An overview of conceptions, characteristics and advanced technologies for big data cloud computing and security issues of data quality and privacy control pertaining to data access, data isolation, data integrity, data destruction, data transmission and data sharing are delivered. In the big data cloud computing environment, data security issues have become a focus of attention. This paper ...
Subsequently, we present how Cloud Computing contributes to IoT-based Big Data, aiming to fill a scientific gap in the sector of their integration regarding security and privacy. Finally, we additionally survey the security challenges of the integrated model of BD and CC and then propose a novel security algorithm for sustainable Cloud systems ...
When we use cloud services, we need to upload data to cloud servers. As the cloud is an open environment, it is easy for attackers to use cloud computing to conduct excessive computational analysis on big data, which is bound to infringe on others' privacy. In this process, we inevitably face the challenge of data security.
Big data conventionally coins large volume of data that continuously increases in a real-time basis and difficult to store, retrieve, and process in traditional database techniques. But it is necessary to know that big data is unstructured and does not follow the conventional storage retrieval methods. The challenges are to store in a cloud, process, and develop meaningful form so that it is ...
Cloud computing is one more field in which most of the ICT services like infrastructure, platform, software, etc. are provided online on demand basis. An important benefit of this service is that ...
The main focus is on security issues in cloud computing that are associated with big data. Big data applications are a great benefit to organizations, business, companies and many large scale and ...
Data is the blood of the network and the core of sustainable development in the information age. The fast growth of the Internet of Things and cloud computing technology has triggered the explosive growth of data scale and the highly complex data model. Big...
Data security is a fundamental component of an organization's cybersecurity strategy. Why Is Sensitive Data Protection Important in Cloud Computing? As organizations use more data, they need to protect its confidentiality, integrity, and availability. Cloud computing models enable collaboration and analytics but present unique challenges.
Blockchain is used to record and distribute information securely. In [44], the authors presented an efficient and secure big data storage system in cloud computing. A leakage-resilient identity-based encryption is used to ensure that the user's data privacy is preserved even if the partial key is leaked in the cloud.
The data controller loses track in Cloud technology since no precise control is accessible whenever information is hosted on the Cloud platform. This shift raises security problems regarding ...
In the big data cloud computing environment, data security issues have become a focus of attention. This paper delivers an overview of conceptions, characteristics and advanced technologies for big data cloud computing. Security issues of data quality and privacy control are elaborated pertaining to data access, data isolation, data integrity, data destruction, data transmission and data ...
From the perspective of the whole life cycle of big data, this paper summarizes the current privacy security risks of cloud computing and big data and divides the risk assessment factors into five stages: data collection, data transmission, data storage, data use, and data destruction, with a total of 22 indexes, as shown in Figure 1. Figure 1.
A Comparative Study on Cyber security Technology in Big data Cloud Computing Environment Abstract: ... the ability of collecting huge amount of data is known as big data analytics. The functions are performed through displaying, interpretation and extraction of the insights of future that can enable early detection of catastrophic cyber threats ...
Among many emerging science and technology, cloud computing and big data are the two most concerned and typical representatives, and the cloud big data platform combining them has become the focus of attention in the field of science and technology, and more and more penetrated into real life. 2. The security and privacy protection of cloud big ...
To have good execution efficiency, most big data analytics are conducted in a distributed environment, instead of a local computer. ... and cloud computing are two dominant distributed environments to conduct big data analytics.In recognizing this new paradigm and opportunities of conducting big data analytics on HPC and/or cloud computing ...
Big Data is a set of technologies based on NoSQL databases allowing scalability of volumes, numbers and types of data. The important companies in the IT sector find these NoSQL systems, new ...
The use of cloud computing has become a reliable information technology solution over the past decade by providing numerous services and resources on a pay-as-you-use basis and evolving from concept to reality. Despite increasing demand and popularity, the adoption of the cloud is hindered mainly by security concerns. Successful cloud adoption and uncomplicated operation are possible if users ...